On Friday, Apple quietly released a patch of what turned out to be a serious iOS security flaw. Five days later, that bug is still very much present in OS X, meaning your MacBook is more at risk than ever. So why hasn’t Apple fixed it yet?
Why This Matters
You can read a more thorough description of the security flaw, known as “goto fail”, here, but essentially it enables bad guys to eavesdrop on your online interactions without resistance. Banking info, emails, Facebook flirtations, all of it susceptible to what’s known as a “Man in the Middle” attack by anyone on the same network (read: same Starbucks) as you.
It’s a major flaw, one that went undiscovered — by Apple, at least — for a year and a half. If you have an iPhone, you should update to iOS 7.0.6 immediately. It includes a patch that fixes the vulnerability. If you have a MacBook, you don’t have that option. If you have a MacBook, you still run the risk of being violated every time you open Safari, Calendar, Facetime or a host of other programs every time you use your MacBook to work from a cafe or kill time at an airport.
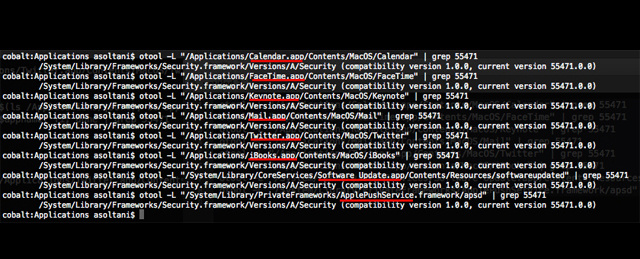
The OS X apps affected by “goto fail;” as uncovered by Ashkan Soltani
It’s also not just a hypothetical; security consultant Aldo Cortesi has already exploited the flaw to take control of an unsettling amount of sensitive information and functionality. And it took him less than a day:
Nearly all encrypted traffic, including usernames, passwords, and even Apple app updates can be captured. This includes:
- App store and software update traffic
- iCloud data, including KeyChain enrollment and updates
- Data from the Calendar and Reminders
- Find My Mac updates
- Traffic for applications that use certificate pinning, like Twitter
It’s difficult to over-state the seriousness of this issue. With a tool like mitmproxy in the right position, an attacker can intercept, view and modify nearly all sensitive traffic. This extends to the software update mechanism itself, which uses HTTPS for deployment.
If that sounds bad, it is. It’s very, very bad. And if Aldo Cortesi can crack it in less than a day, imagine what a dedicated malfeasant can do with four and counting.
Why the Delay?
On the face of it, it’s confounding that there’s no OS X fix yet. Especially since while it’s an extremely serious issue, it’s also on the face of it a fairly simple error. All it took to fix iOS was to extract a single line of errant code, and presto! iPhones were once again safe.
So why the hold-up on OS X? An Apple spokesperson told us that they “are aware of this issue and already have a software fix that will be released very soon,” but declined to go into further detail. There are a couple of plausible theories, though, neither of which is pretty.
It’s Complicated
While it was easy enough to fix “goto fail;” in iOS, it’s entirely possible that the OS X version requires a little more muscle than extracting one line. That’s the theory security researcher Ashkan Soltani is going with:
To be fair to Apple, that they’ve taken this long to release a patch OSX suggests it’s more than a one-line fix. Prob regression testing++
— ashkan soltani (@ashk4n) February 24, 2014
Reasonable enough! But Cortesi takes it one step further. Let’s look at the last bit of that blockquote from him again:
With a tool like mitmproxy in the right position, an attacker can intercept, view and modify nearly all sensitive traffic. This extends to the software update mechanism itself, which uses HTTPS for deployment.
Emphasis added this time. What this means is that Cortesi was able to intercept not just whatever passwords are exchanged between you and your bank, but App Store traffic itself. And guess where the OS X update that fixes this mess will come from? The App Store.
To put this in the plainest possible terms: It’s possible that while Apple has a fix in place, it doesn’t know how to get it to you safely. Yes, you can download it over a secure network and be fine. But if you tried to download it over public Wi-Fi, it wouldn’t take much for a hacker to impersonate the App Store and send you the malware of their choice. Since Apple can’t guarantee that every download happens in a secure environment, it’s a Catch-22.
Two Birds, One Update
The other popular theory is that while Apple has a fix in place, it’s waiting to fold it into a larger update.
The screenshot below, from AppleInsider, shows a prerelease build of OS X 10.9.2, an impending update for your MacBook and iMac’s operating system. It lists the usual sorts of fixes you’d expect to find; reliability, accuracy, adding small features. What you don’t see, though, is that 10.9.2 reportedly fixes the security flaw in question.
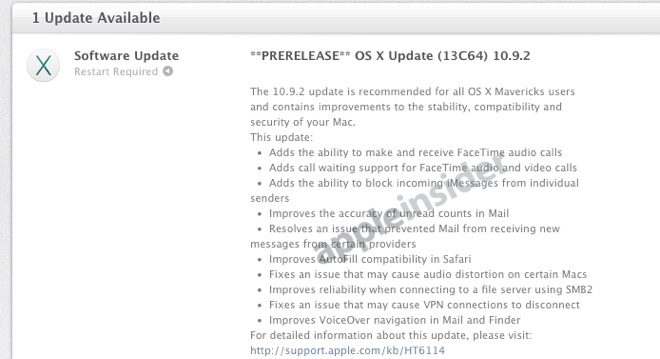
In one sense, it’s definitely more efficient for Apple to ask its customers to update OS X once to fix a host of issues instead of twice in rapid succession. Updates are annoying!
But forestalling a major security fix for the sake of efficiency seems ill-adviced. Think of it this way: You have a number of cosmetic repairs you’ve been wanting to make to your house. Fixing up a paint job in the living room, tidying up the kitchen, maybe cleaning out the gutters. Suddenly, the curtains in your dining room catch on fire. You might think that everything else can wait until you put that fire out; with OS X, if this report is true, it appears that Apple is making sure it’s got the right pantone first.
The security community is, as you might imagine, not thrilled at the prospect:
Apple, you have GOT to be fucking kidding: Wait for 10.9.2 for #gotofail fix? WTF? http://t.co/AhfxxTDcmV
— Nicholas Weaver (@NCWeaver) February 24, 2014
If you believe call waiting, message unread counts, voiceover navigation, etc. are worth leaving SSL broken for, you need to retire.
— Ryan Lackey (@octal) February 24, 2014
Unacceptable. http://t.co/AbWxtvizqO How do we get Apple to pay attention? Start showing up en-masse to clog the genius bar demanding a fix?
— hillbrad (@hillbrad) February 24, 2014
Who the fuck at Apple decided to wait for 10.9.2 to patch the SSL vulnerability? http://t.co/FxYiQGPsy0 #OSX #gotofail
— Koen Rouwhorst (@koenrh) February 24, 2014
We’ve reached out to Apple for more clarity about the timing of the patch, and specifically whether it’s pegged to OS X 10.9.2. But what’s most likely is that it’s a combination of these two factors; it’s a more complicated bug to patch — and more importantly, to deliver to customers — than you’d think, and the timing lines up closely enough with a release Apple was going to push out anyway that it made sense to combine the two.
Who knows? It’s entirely possible that 10.9.2 is being delayed until the bug is fully fixed, and not the other way around.
How Can I Protect Myself?
If there’s one thing you can be frustrated with Apple about through all this, it’s that they haven’t been particularly communicative. As far as security flaws go, this is a big deal, but there are ways to keep yourself safe that haven’t been widely publicised by Cupertino.
First, again, if you’re on iOS you should download 7.0.6 immediately. Do not pass Go, do not collect $200. Once you do, your iPhone and iPad are fine.
If you’re on OS X, the most important thing is not to do anything remotely sensitive over public Wi-Fi. That’s a good rule of thumb regardless, but it’s especially important while this vulnerability is in the wild. Stick to your protected home network if you can, you’ll be fine. And, if you can’t, use Chrome or Firefox — which use a different security protocol — for your browsing needs.
And when that OS X patch does happen — whether as part of 10.9.2 or as its own update — be first in line to download it. Just, you know, not from a cafe.
