There’s an ever-growing list of ways mobile devices can be hacked, which means we have to be increasingly vigilant about security. But now even something as innocuous-seeming as leaving your phone sitting on a table can result in a hack. Researchers just demonstrated that someone can gain access to your phone by hacking its smart assistant through voice commands inaudible to humans.
The SurfingAttack, as the attack is called, was developed by a team of researchers from Michigan State University, the Chinese Academy of Sciences, the University of Nebraska-Lincoln, and Washington University in St. Louis, Mo. The research itself is detailed in a recently published paper. Essentially, if you’ve ever heard your phone loudly rattle on a table when its silent alarm goes off, you’ve already experienced how this attack works.
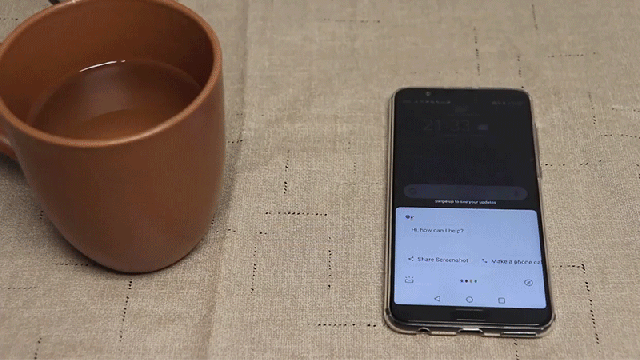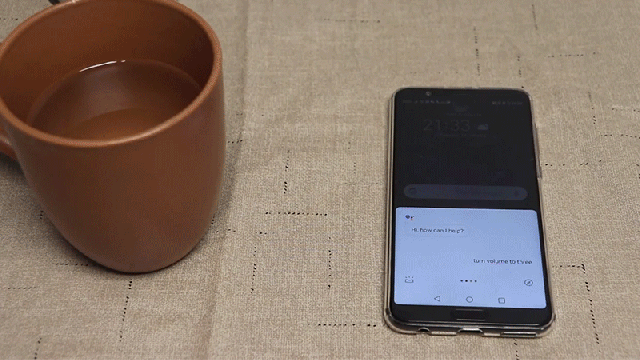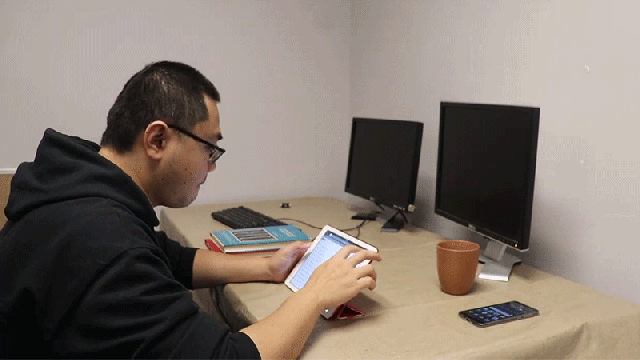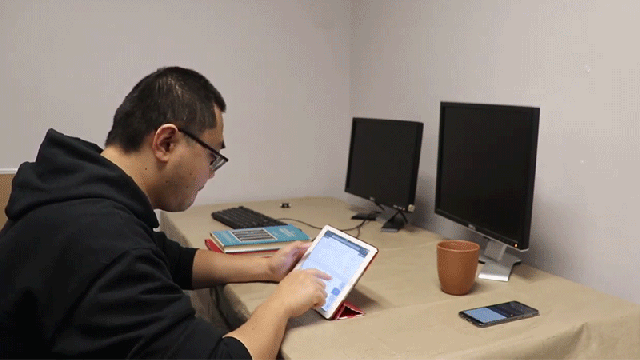
There is some special hardware required, but the key ingredient is an $8 off-the-shelf piezoelectric transducer that’s able to generate vibrations that fall outside the range of human hearing. When connected to a signal generator and then mounted to a thin piece of glass or metal that can be hidden underneath a tablecloth, the transducer can impart ultrasonic vibrations, causing the material to vibrate and generate sounds that people can’t hear. The sounds aren’t just tones; they can also be words and instructions that the sensitive microphones on mobile devices can easily detect, triggering a device’s smart assistant when it’s been set to respond to voice commands.
Maybe you’re thinking: “So what? Hackers can use my phone to check the weather, who cares?”
But unfortunately, smart assistants have become so integrated into the operating systems of mobile devices that hackers can pull off some pretty irritating stunts: placing long-distance calls that quickly rack up unwanted charges and hijacking text messages, which could potentially give hackers access to verification codes if your phone number is used as part of a two-factor verification process.
The SurfingAttack process also relies on a hidden nearby microphone to listen for responses from a target device’s smart assistant, or text messages that can be read aloud using hands-free options designed to be safer for drivers. After making contact with a smart assistant, additional commands can be passed along to reduce the smartphone’s volume so that it’s too quiet for someone in a bustling office to actually hear their device having a one-way conversation, allowing the hack to potentially go unnoticed for several minutes—perhaps even longer if the device’s owner is distracted.
Some materials work better than others at conducting the ultrasonic signals to a device, but the researchers used an aluminium plate to pull off the SurfingAttack from a distance of 30 feet, allowing the other required equipment to be easily hidden out of view. They found several ways to thwart the attack, however, in addition to just disabling your smart assistant’s always-listening feature and requiring it to be triggered manually. Thicker tablecloths muffle the ultrasonic signals to the point where voice commands can’t be understood by a device, as do beefier smartphone cases designed to protect against falls and absorb impacts. And just think: All your friends once laughed at you for using an ugly phone case.