A critical flaw in electronic locks left millions of hotel rooms worldwide vulnerable to hackers. Now, the security researchers who developed the attack are helping hotels patch the problem, literally door to door.
Tomi Tuominen and Timo Hirvonen, who both work for the international cybersecurity firm F-Secure, uncovered a design flaw in the software of electronic keys produced by VingCard, a global provider of hotel locking systems. By F-Secure’s count, the vulnerable software, Vision, is deployed in as many as 166 countries at over 40,000 buildings – millions of doors, in other words.
While hijacking and cloning hotel room keys is nothing new, the attack designed by Hirvonen and Tuominen is exceptional for a few reasons: First off, it allows the attacker to produce a master key for the entire building within a matter of minutes. All that’s needed is a regular hotel room key. It can even be expired.
“It can be your own room key, a cleaning staff key, even to the garage or workout facility,” Tuominen told Gizmodo. “We can even do it in an elevator if you have your key in your front pocket; we can just clone it from there.” Tuominen compared the following step to a scene in Terminator 2, in which John Connor brute forces open a safe open with (movie trivia alert!) an Atari Portfolio palmtop computer, circa 1989.
“We are doing exactly the same,” Tuominen said.
The obsession with cracking hotel room keys began in 2003, the pair said, after attending PH-Neutral, an invite-only hacker conference in Berlin, formerly run by the hacker FX. One of Tuominen and Hirvonen’s colleagues returned from the conference to find his hotel room breached and his laptop stolen. But there was no sign of forced entry, so the hotel staff wasn’t buying it.
Since staff keys typically work throughout the building, hackers usually target cleaning staff or managers whenever attempting to clone a key that can open any room in the hotel. Keys that use RFID, or electromagnetic fields, for instance, can be cloned easily without raising suspicion. Even just walking by hotel staff with an RFID reader concealed in a messenger bag is usually enough to capture a card.
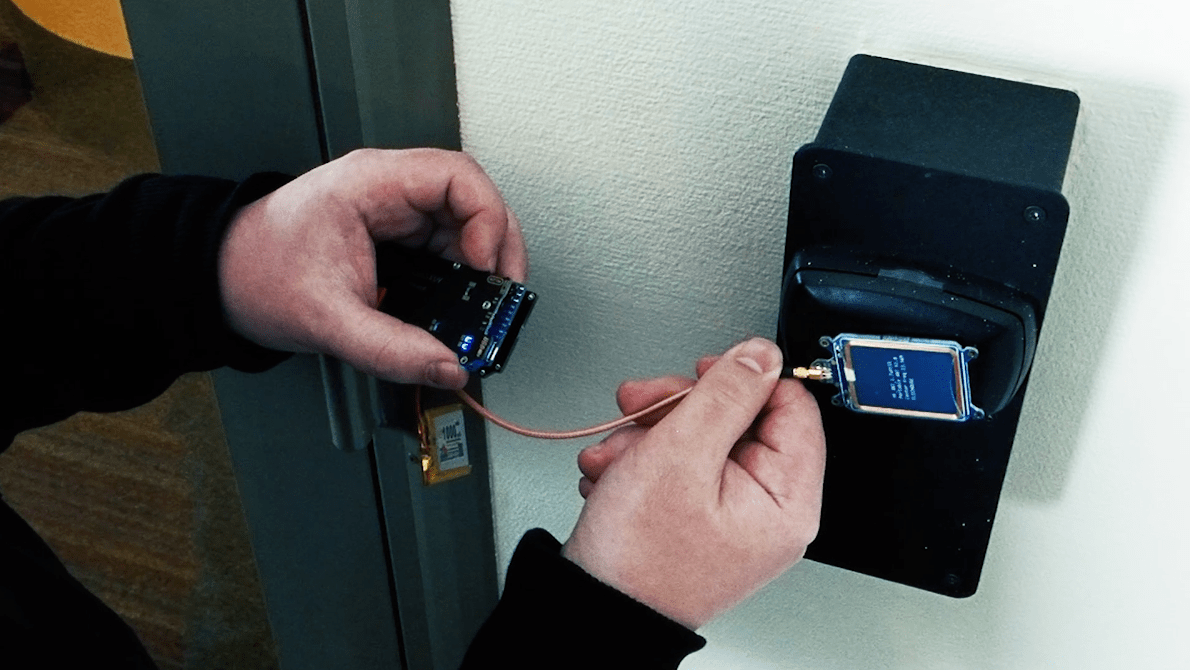
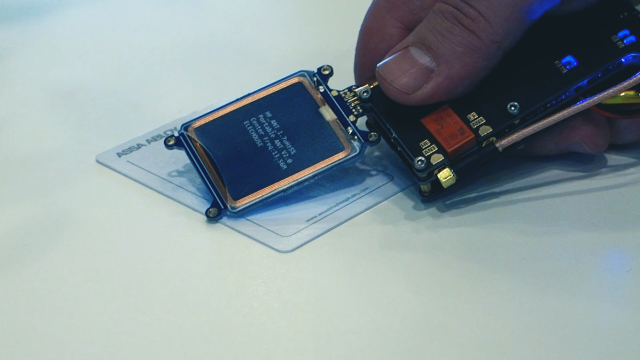
After capturing a card, the process of creating a master key requires burning through on average 20 key combinations on a hotel RFID reader. A minute is usually long enough to complete the process.
The card’s response to the reader can be recorded and duplicated later, by creating a new card (a clone) or by using some other tool, such as a Proxmark3, that can emulate the same radio frequency and unlock doors. The attack designed by F-Secure’s research, however, allows for the creation of a master key from any hotel room key, so long as it uses VingCard’s Vision software, which, as mentioned, millions do.
According to the firm, the attack is an original concept, not a variation on previous methods (such as so-called nested authentication or dark-side attacks commonly used against Mifare cards).
“The magic happens on the software layer, which we made ourselves,” Tuominen said. The researchers used modified Proxmark firmware in their demonstrations, but once a card was captured and the master key created — a process they have been able to replicate in under a minute — nearly any RFID token, inserted into the smallest of objects, could be transformed into a hotel master key.
At the same time, the attack isn’t so trivial. “You can’t just copy blindly. It won’t work,” Hirvonen said. “A typical RFID cloner won’t do the trick.”
Unfortunately for those interested in learning more about the technique, F-Secure has decided not to disclose it, citing concerns that it may be used maliciously as hotels are still in the process of fixing affected doors. “We can’t tell all the details because we want to protect the innocent,” Tuominen said.
The hospitality industry is a prime target for hackers, according to virtually every security firm that studies patterns of attacks.
What’s more, Hirvonen and Tuominen’s discovery didn’t stop at the hotel’s doors. “Tomi and Timo also found that the Vision software could be exploited within the same network to get access to sensitive customer data. A malicious actor could download guest data or create, delete, and modify guest entries,” F-Secure said.
“It’s a totally separate attack in the very same system,” Hirvonen told Gizmodo. By unplugging the network cable from a hotel receptionist computer, the researchers found they were able to gain full access to the VingCard server, where all the content relevant to the keys is kept, including to whom they are assigned.
F-Secure reported that its experience in dealing with VingCard – the company’s name today is Assa Abloy – went exceptionally well. “They were very open-minded,” Tuominen said, adding that VingCard’s CTO and head of engineering turned up at their first meeting. “I’d like to think they took us very seriously from the beginning,” he said.
The company was eager to learn more about the attack and how to stop it, so much so that a demo environment was set up for the researchers to show off their skills. Over the course of the past year, F-Secure said it worked closely with Assa Abloy to develop a solution that the researchers couldn’t easily bypass.
“We have had a very good relationship with their R&D team,” Tuominen said.
In a statement, F-Secure thanked Assa Abloy, the door security company that helped them work out a solution to the flaw. “Because of their diligence and willingness to address the problems identified by our research, the hospitality world is now a safer place,” Tuominen said. The firm is urging every hotel using the Vision system to deploy the patch to keep their guests, and their property, safe.