In software, there are bugs, and there are dangerous bugs. It looks like macOS High Sierra has one of those dangerous bugs; one that could give someone full access to virtually any user account. And holy buckets, it is scary.
All images: Gizmodo
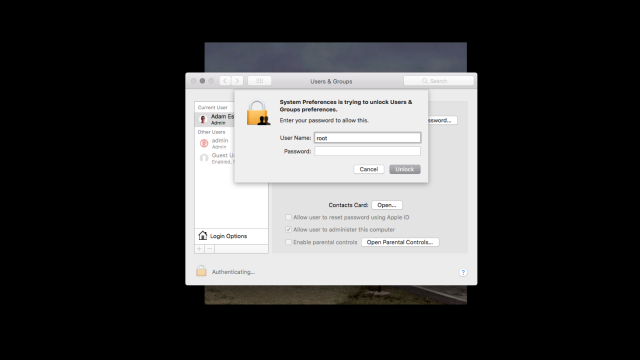
Turkish software developer Lemi Orhan Ergin pointed out an apparent macOS security vulnerability in a tweet this morning. Basically, if you open System Preferences and then navigate to Users and Groups, you can easily gain access to make changes to any account on that machine. Just click the lock, and when macOS prompts you for a password, replace the user name with “root”, select the password field (but don’t type in a password), and click Unlock. Just like that, the system will unlock. We were able to replicate the issue multiple times. (Seven attempts seems to be the sweet spot.)
It’s important to highlight the fact that a hacker would probably need access to a logged in Mac in order to take advantage of this vulnerability. If there’s a root user already enabled, the macOS login screen does not let you change the user name.
But Gizmodo reader wrote in with an even more terrifying possibility:
If you have Remote Management enabled in your Sharing preferences then someone with Apple Remote Desktop or screensharing.app can in fact log in remotely using this exploit. I’ve confirmed this behaviour personally with a friend at my co-working space, and it’s been confirmed here as well.
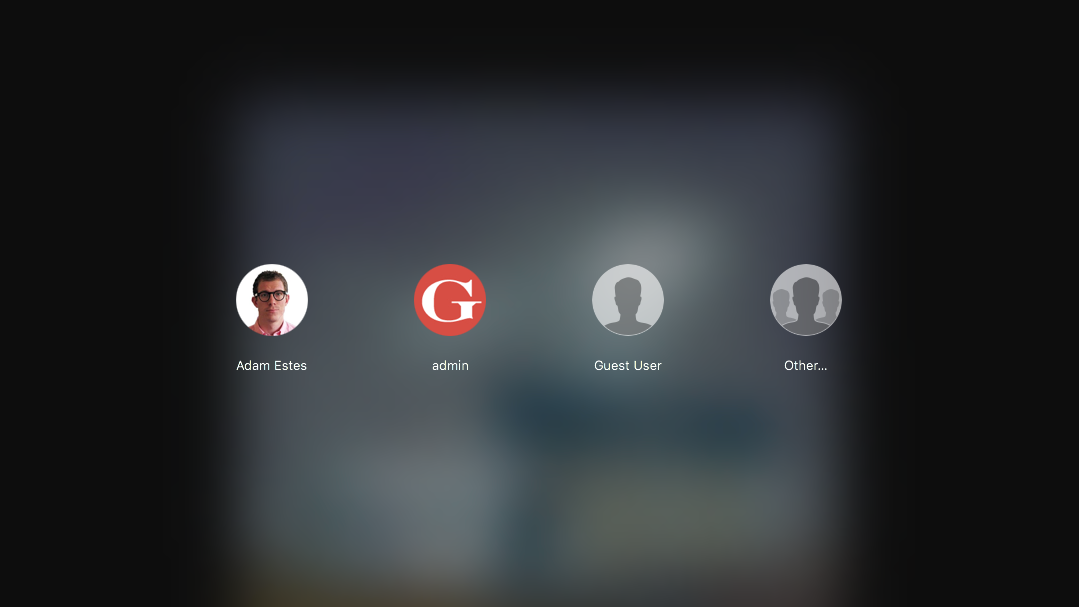
If you’ve used the trick to unlock the Users and Groups already, you can use the same “root” trick to log back into the computer after you’ve logged out. Just select the Other as a user, type in “root”, click the password field, and then hit return. This will set up a new user and let you use the machine as an admin. As Macrumors points out, you can prevent this by enabling a root user on your Mac.
We reached out to Apple to learn more about this bug, its scope, and how the company plans to address it, but had not heard back at time of writing.