At least tens of thousands, if not millions of medical records of New York patients were until recently readily accessible online to just about anyone who knew how to look.
Photo: Getty
Patient demographic information, social security numbers, records of medical diagnoses and treatments, along with a plethora of other highly-sensitive records were left completely undefended by a medical IT company based in Louisville, Kentucky. The files, which belong to at least tens of thousands of patients, originate from Bronx-Lebanon Hospital Center in New York.
In a statement provided to Gizmodo — and published by NBC News Thursday morning — Bronx Lebanon said that a server containing its patients’ data had been the “target of an unauthorised hack by a third party”, attributing that assessment to the hospital’s vendor, iHealth Solutions. The hospital added that iHealth had taken immediate steps to protect the data, and that both parties were “cooperating fully with law enforcement agents”. iHealth Solutions did not respond to request for comment.
However, according to Kromtech Security Center, a German security software development firm, the leak was not the result of a malicious hacker infiltrating the Bronx Lebanon server. Instead, the firm’s analysis showed that the data was left unprotected on a backup storage device, without a password, accessible to anyone online. It also appears likely that the data was not protected by an active firewall, exposing an untold number of patients to crimes such identity theft and blackmail.
Receiving roughly 1.1 million visits per year, according to its website, Bronx Lebanon is the largest not-for-profit hospital in the South and Central Bronx, complete with psychiatric programs, two specialised long-term care facilities, and network of smaller medical practices. In total, the system contains 972 beds. Its emergency room, one of the busiest in New York, sees an estimated 140,000 visits per year, according to its website.
Among those most vulnerable are an untold number of patients who’ve checked in to one of Bronx Lebanon’s chemical dependency programs. The leaked files, which have reportedly now been secured, contain a considerable number of addiction intake forms. The security researchers who stumbled across the data tell Gizmodo the documents “paint a full picture of the patient’s drug use, medical history, and suicidal thoughts”.
The exposed Bronx Lebanon files were first reported by Kromtech, which says it discovered the cache while conducting an independent security audit. Despite the hospital’s insistence that it was the victim of a cybercrime, forensic evidence collected by Kromtech tells a different story — one that could implicate iHealth Innovations in a serious violation of the Health Insurance Portability and Accountability Act (HIPAA), the US federal law which governs the security standards for the protection of electronic protected health information, if it proves true.
Among other technical safeguards, HIPAA requires that health care providers implement mechanisms to encrypt confidential medical data, to protect it from alteration or destruction, and to “guard against unauthorised access to electronic protected protected health information this being transmitted over an electronic communications network”. Those authorised to handle sensitive medical records are also required under the law to provide notification of a security breach involving the disclosure of personally identifiable health information.
Fines for violating HIPAA’s provisions can be steep. Last year, the University of Mississippi Medical Center paid out $US2.75 million ($3.7 million) after a laptop disappeared from an intensive care unit. Unlike the data contained on the Bronx Lebanon server, the patient files on the stolen Mississippi laptop had the benefit of being protected by a password.
According to Kromtech, the Bronx Lebanon “data breach” allegedly occurred because its backup storage device was essentially configured to allow anyone to view the files. In this situation, for an average user, the files would not have been easy to locate. But for malicious hackers and legitimate security professionals, it’s no trouble at all.
To locate the Bronx Lebanon data, one would only need to initiate a search for devices running Rsync, a common file transfer protocol primarily used for backing up data. And there’s a good reason why Kromtech conducted this search: There have been numerous major leaks caused by misconfigured devices running Rsync with its default port unprotected. While in the course of its audit, Kromtech reports researchers discovered that the Bronx Lebanon server had fallen victim to this common user error.
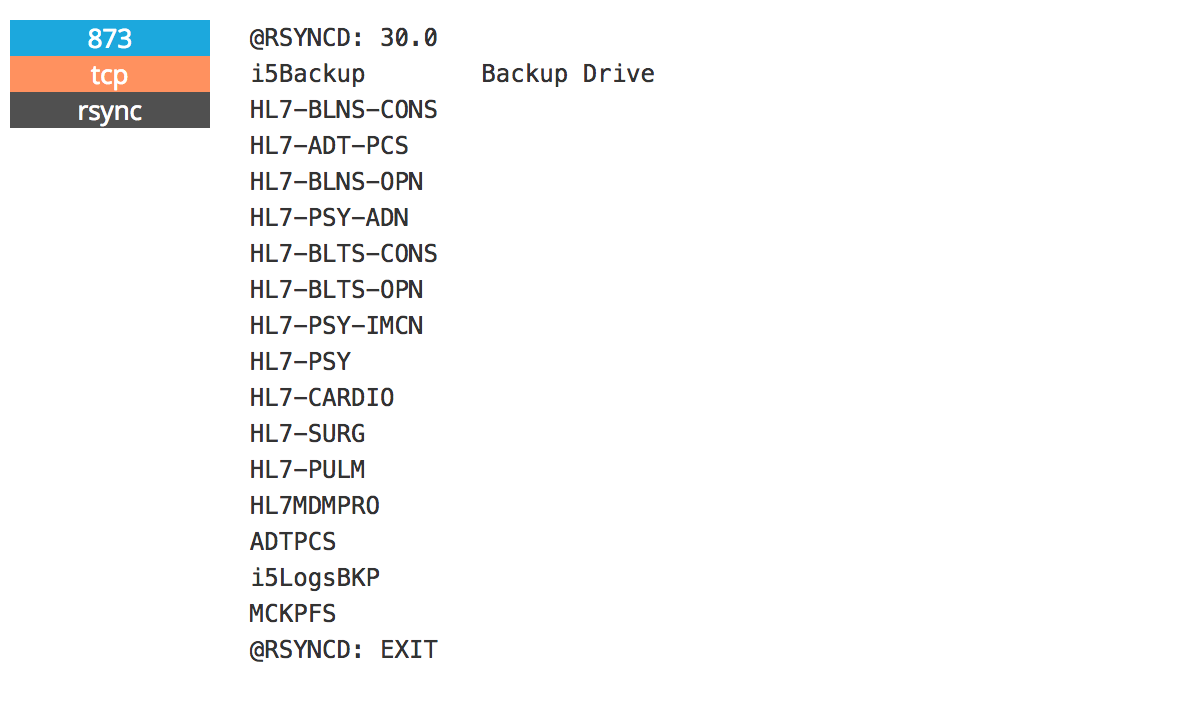
A screenshot from a cached Shodan search shows a hospital file directory accessible via Rysnc on port 873.
Using Shodan — a search engine that crawls not only websites, but all networked devices — researchers discovered that iHealth Solutions left the default Rsync port (873) unsecured. The file directory below shows folders apparently for various departments of the hospital, including surgery, psychiatry, cardiology and pulmonology.
According to Bob Diachenko, a cybersecurity specialist at Kromtech, one of the folders discovered online — which was not encrypted — contained more than 300 text files, with file sizes ranging from 4MB to 473MB. A single file of average size (34MB) contained the medical data of more than 7000 patients.
If we do a little envelope maths, it isn’t hard to see why this leak could be of such concern. A 34MB text file would contain roughly 29,000 pages, or an average of four pages per patient.
Ultimately, it’s a ton of records, but the number of patients affected is known only to iHealth and Bronx Lebanon. Estimates by Kromtech say there are at least tens of thousands. The data files only date back to 2014, but it’s unknown whether older medical records may have been digitised and uploaded that year. Files for the same patients may also be contained in multiple folders.
Gizmodo began placing calls to Bronx Lebanon on Tuesday, but the staff members who answered the phone said they were not authorised to discuss the breach. The hospital’s statement, alleging an “unauthorised hack”, arrived Wednesday.
Security researchers are often accused of being “hackers” when contacting random companies to report flaws in their security. Unfortunately, this has also been the case at Kromtech, even though in the last year the company has helped secure countless breaches at US-based businesses.
In March, Kromtech reported that more than 400,000 audio recordings of telemarketing calls had been exposed online, including many in which customers provided sensitive information, such as credit card details. A month before, the researchers helped secure the personal data of nearly 25,000 California sheet metal workers. Before that, it was a Missouri sheriff’s office, which had inadvertently leaked audio recordings of police informants of victims involved in crimes as serious as child molestation.
It may also be the case that by the time Kromtech reported the breach to iHealth Innovations, the data had already been stolen by someone else. That would significantly increase the risk of identity theft or worse to the patients of Bronx Lebanon.
On Thursday, a hospital spokesman called to say that it was sticking by the “unauthorised hack” story offered by iHealth. Asked about the forensic evidence collected by Kromtech, which appears to contradict iHealth’s version of events, the spokesman twice replied: “We stand by our statement.”
