A ransomware gang claims to have stolen over 100 gigabytes of data from Jones Day, a prominent global law firm that recently stirred backlash for its entanglement in the 2020 presidential election.
The hacker group CL0P has posted a large tranche of stolen files to a dark web “leak site,” claiming it snatched them from the law firm during a recent cyberattack. Such sites will typically be used by hackers to goad a victim into paying a ransom. CL0P’s site is publicly available and has been independently verified by Gizmodo.
The breach was initially reported by Databreaches.net. According to reporting from the Wall Street Journal, CL0P claims to have reached out to the law firm about the hack, in an apparent bid to initiate ransom negotiations:
The hacker, in the Journal’s correspondence, said it first reached out to Jones Day management on Feb. 3 and informed the firm that its network had been hacked and that data had been stolen. As of Tuesday, the hacker said Jones Day management hasn’t responded but that it believes the law firm received its letters about the attack. The hacker said ransom negotiations haven’t begun.
For background, CL0P is a prolific ransomware family with a growing list of victims. Last year, hackers used its malware to pilfer data from numerous large companies and other organisations — hacking into technology firms, a South Korean retail giant, and an international flavour developer, among others.
Still, Jones Day sticks out in CL0P’s apparent victim pool for its size and prominence. The Cleveland-based law firm, originally founded in 1893, has an annual revenue of over $US2 ($3) billion and has represented the likes of Walmart, Goldman Sachs, and McDonald’s. It has also occasionally raised eyebrows by representing slightly more notorious characters (read: businesses connected to Russian oligarchs, Big Tobacco, and the Bin Laden family, among others).
Most recently, Jones Day garnered criticism over its involvement in one of the legal battles related to vote counting in the 2020 presidential election. The decision led to widespread accusations that the firm was “aiding” and “enabling” Trump’s efforts to delegitimize the results of the 2020 presidential election — claims it has staunchly refuted. Despite these refutations, the ongoing, close relationship Jones Day lawyers have had with Trump since the beginning of his presidency is undeniable. The New York Times reports that “Jones Day has been one of Mr. Trump’s most steadfast legal advisers,” with its attorneys working for him in various positions as far back as 2016. Firm partner Don McGahn even played a fraught role in the Mueller investigation.
Putting all this aside and returning to the cyberattack, there is no evidence that any of the recently leaked data has anything to do with the work the firm did on behalf of Trump or his related activities. That doesn’t mean there aren’t truckloads of sensitive data now floating around the dark web that Jones Day will have to try to account for.
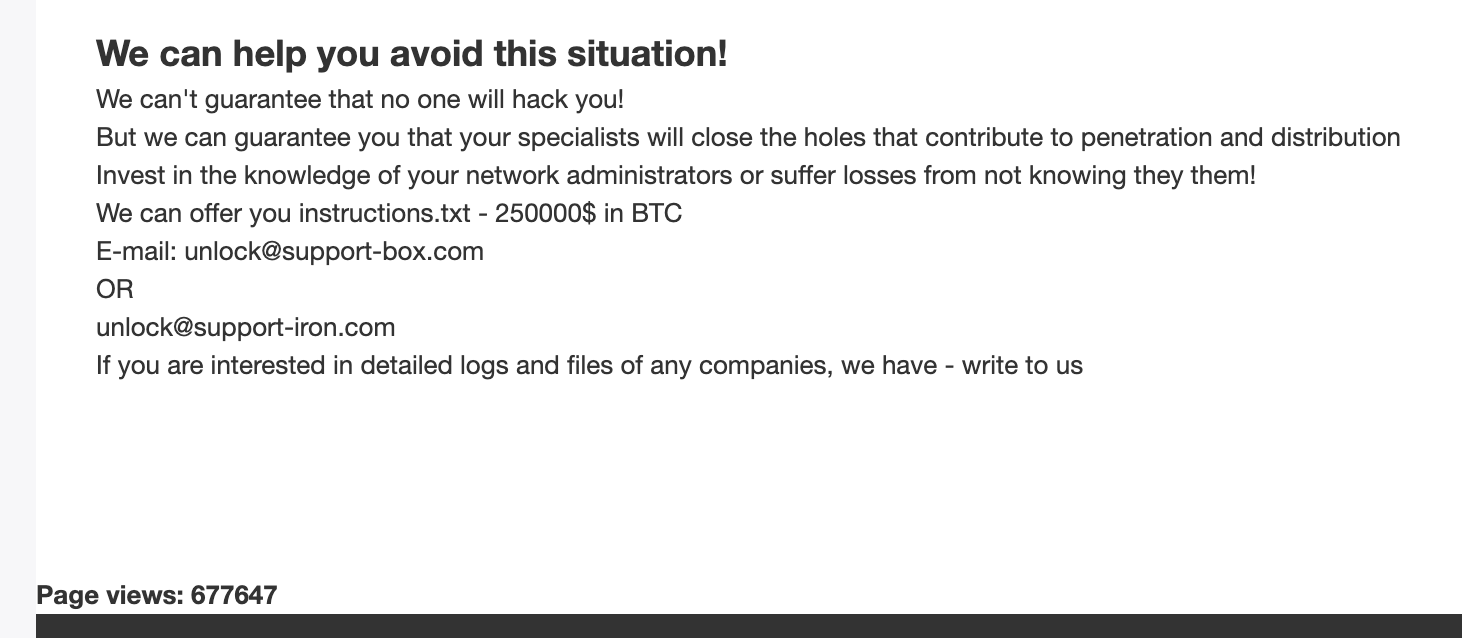
Interestingly, the firm has actually refuted CL0P’s version of how its data was stolen. The firm rejects the notion that its networks were breached in a ransomware attack. Instead, it says it was the victim of a third-party data breach via the embattled firm Accellion, according to statements made to the Wall Street Journal. This is in direct contradiction to what CL0P told the Journal, which is that it had “hacked Jones Day’s server directly and that it wasn’t involved in the Accellion hack.”
For those who don’t know, Accellion is a cloud provider that, in January, reported it had been the victim of a series of cyberattacks. The vector for the attacks was the company’s secure file-transfer application (called “FTA” for short), a legacy, end-of-life product that, at the time of the intrusions, was still being used by as many as 300 clients, including banks, university systems, government agencies, and large corporations. In December, Accellion discovered that a threat actor had been leveraging a zero-day vulnerability to conduct a “highly sophisticated attack” on the FTA. Accellion notified customers and patched the security hole, but soon discovered there were more.
[referenced id=”1671782″ url=”https://gizmodo.com.au/2021/02/the-accellion-data-breach-seems-to-be-getting-bigger/” thumb=”https://gizmodo.com.au/wp-content/uploads/2021/02/12/ppgvylpiegvugrkqbi67-300×169.jpg” title=”The Accellion Data Breach Seems to Be Getting Bigger” excerpt=”Data breaches have a tendency to grow past initially reported figures. Organisations don’t always know how screwed they are right away, investigations take time, and new victims are discovered amidst the wreckage. This is certainly proving to be the case with Accellion, the Palo Alto, Calif.-based cloud provider that experienced…”]
Accellion initially announced that only about 50 of these clients had been affected by the attack, but that number has since grown. Interestingly, a number of Accellion clients that recently reported data breaches in connection to the hack are listed on CL0P’s leak site. Those include Singtel (a large Singapore-based telecom) and Fugro (a vast Dutch geospatial data firm).
While it might seem like a logical conclusion from the Jones Day incident that CL0P is the threat actor behind the Accellion data breach, Emsisoft security analyst Brett Callow said it’s not quite as simple as that. In reality, there are a number of possibilities: the data could have been stolen by another threat actor and sold to Accellion, or some other series of events could have delivered it into their hands — assuming the data is legitimate at all.
“If [Jones Day] is correct in saying the data leaked via Accellion’s FTA file transfer platform, then it would seem likely that Clop was either responsible for that attack or obtained the data from whichever group was,” said Callow. “Whatever the case, that could spell trouble for the other organisations breached via the FTA. Either Clop may have their data or an unknown third-party may [be] attempting to sell it,” he said.
We have reached out to Jones Day and Accellion for comment on this story and will update this post when we hear back.
Editor’s Note: Release dates within this article are based in the U.S., but will be updated with local Australian dates as soon as we know more.
