The California Department of Motor Vehicles has warned state residents that over a year’s worth of data — including customer addresses and licence plate numbers — may have been compromised in a recent cyberattack on a third-party contractor.
That contractor — Automatic Funds Transfer Services (AFTS) — is a financial services and data management firm, which California uses to verify changes of address for car owners.
AFTS was hit by a ransomware attack sometime between Feb. 3 and 4, potentially exposing “the last 20 months of California vehicle registration records that contain names, addresses, licence plate numbers and vehicle identification numbers (VIN),” the DMV has said. As should be obvious, that means millions and millions of records.
When reached by phone Thursday, a DMV representative said it was unknown whether data had actually been viewed or stolen in the attack. The agency has emphasised that “social security numbers, birthdates, voter registration, immigration status or driver’s licence information” have definitively not been compromised, as they were not shared with the contractor. Law enforcement agencies have also been notified and are involved. AFTS couldn’t immediately be reached for comment.
As bad as this all sounds, the situation may, in fact, be much worse. As TechCrunch reports, this firm is used “across the United States,” so the breach may extend far beyond the cramped, dirty halls of the Golden state’s motor vehicle offices and affect many other organisations. Indeed, public entities in about a dozen communities have already reported potential breaches related to the ransomware attack. More on that in a minute.
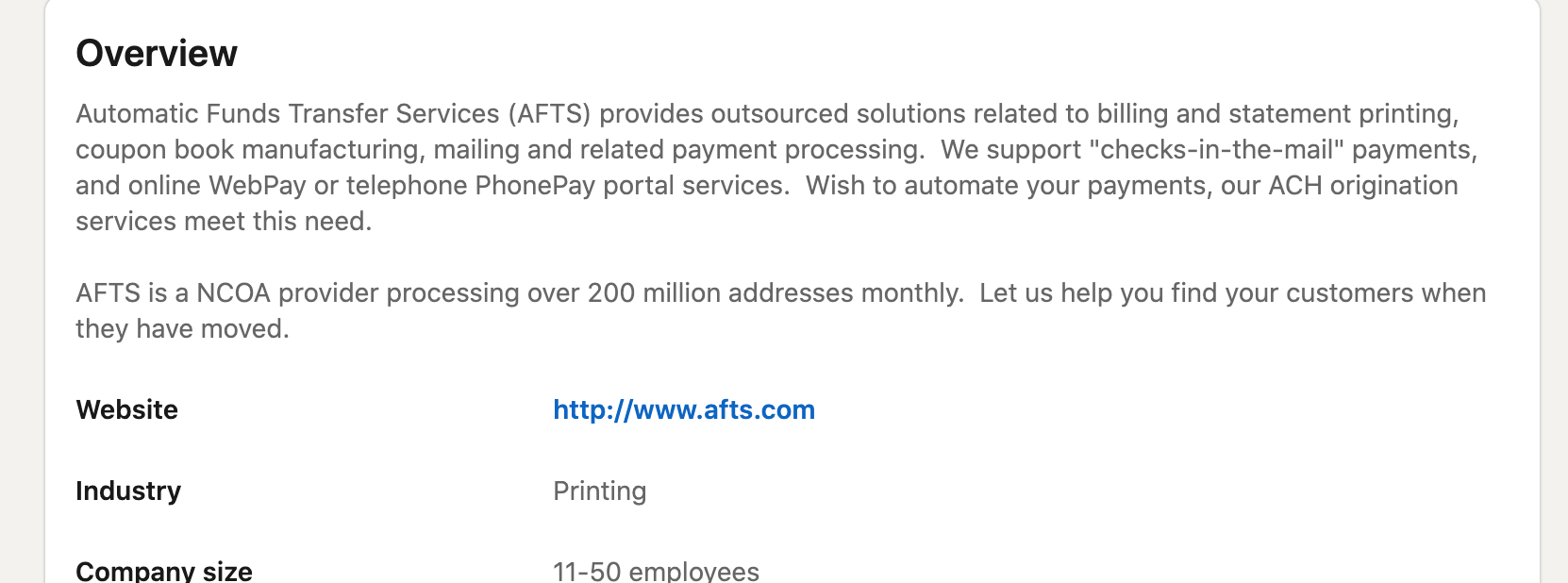
Just looking at AFTS gives a better sense of the potential scope of the problem here. The company’s site is currently down, running only a white page that says:
“The website for AFTS and all related payment processing website are unavailable due to technical issues. We are working on restoring them as quickly as possible.”
On the Wayback machine, however, you can get a sense of what its old website looked like circa 2019:

As you can see, AFTS handles a lot of financial data, advertising itself as a source for “payment processing solutions.” In 2019, the company offered services for invoicing, rental collection, mobile payments, contract loans, and 1031 tax-deferred exchanges, among other things. Since this is an older version of the website, it is unclear whether the company still performs all of these services. However, the firm’s Linkedin profile similarly shows the wide variety of financial data it handles:
Since AFTS hasn’t put out a statement about the attack that details all of the clients and data affected, it’s impossible to know how bad this actually is.
Here’s what is known, however: the California DMV isn’t AFTS’s only public sector client. The firm seems to contract with a lot of public agencies in a lot of different cities — particularly in Washington state — most of which use it for bill pay services. This means that there is a real danger of sensitive financial information having been exposed. A number of cities have stepped forward over the past few weeks to explain this to constituents.
One of the biggest of these is Seattle, which made it known yesterday that it contracts with AFTS. The city said Wednesday:
City departments use this vendor for commercial billing, printing, and mailing services. Seattle Information Technology Department leads, including security and privacy teams, are working with AFTS, affected departments and the City Attorney’s office to understand the potential impact of this incident on personal information.
Another city, Redmond, Wa., home to Microsoft and Nintendo, announced earlier this month that it contracts with AFTS for utility bill payment services. A statement reads.
Personal information may have been exposed including names and addresses of utility customers. The City of Redmond is working closely with AFTS to determine the extent of the breach and if any of the City’s information was compromised.
The city of Kirkland, Wa., too, recently announced it had been potentially affected by the breach: “Kirkland contracts with AFTS to handle Kirkland residential and commercial utility billing and the processing of paper check payments,” officials recently announced. Potentially affected data includes:
utility bill account number, name, address, and billing amounts. Additionally, for residents who pay their utility bills by mailing a paper check, scanned copies of their paper checks are also stored on the AFTS servers – which include bank account and routing information.
Public entities in the Washington communities of Monroe, Alderwood, Lakewood, Everett, Silver Lake, and others, have all posted similar notices.
So, yeah, yikes. Because it’s unclear how many clients AFTS has and what kinds of data was potentially compromised in the attack, it’s also unclear how big this data breach is. When looking at the known clients and the kind of information they were sharing with AFTS, however, it’s obvious why this kind of organisation would be viewed as an appealing target by ransomware hackers.
The incident also seems to reiterate the fact that third-party vendors are a very big security conundrum for public agencies (see the ongoing Accellion mess and how it, too, has affected Washington), as a single, successful attack can spawn a data breach with a very wide net.
