Ransomware operators are closing out a year of extorting local governments, hospitals, and schools across the country with a bang, with at least four more U.S. cities falling victim to sophisticated scams this month alone and a recent report tallying the total number of incidents at nearly a thousand.
In Pensacola, Florida, a cyberattack using the Maze malware and demanding $US1 ($1.5) million in ransom forced city officials to disconnect many machines from the network to prevent the infection from spreading.
Florida Department of Law Enforcement officials said that the attack appeared to involve the same Maze malware as a separate incident targeting security company Allied Universal in November.
New Orleans declared a state of emergency on December 13 after being hit hard with another variant called Ryuk, affecting at least 4,000 city computers. On Thursday, Mayor LaToya Cantrell announced that damages had exceeded the city’s $US3 ($4) million cyber insurance policy and that New Orleans would be increasing its coverage to $US10 ($15) million next year.
In Galt, California, a suburb of Sacramento, Galt interim City Manager Tom Haglund told reporters on December 17 that ransomware had corrupted both their email server and telephone systems, resulting in a “significant impact” and forcing city employees to communicate via text messages and personal emails.
Finally, in St. Lucie, Florida, ransomware targeting the county sheriff’s office took IT functions such as emails, fingerprinting, jail visitation, and background checks offline, according to TCPalm. Sheriff Ken Mascara declined to name the malware involved, but told reporters on Dec. 17 that operations were largely continuing as normal and the department was “pretty confident we should be up and running within a couple of days.”
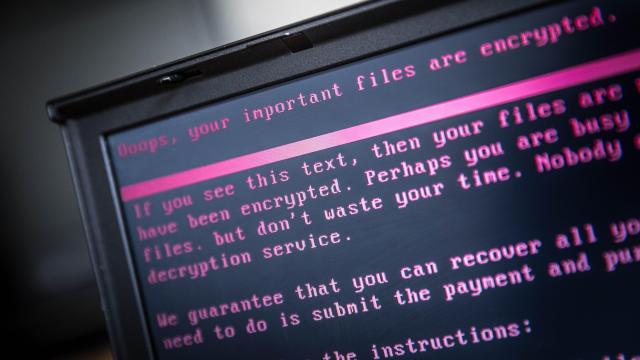
Ransomware works by gaining access to a given network, often through methods like phishing, before spreading a malicious payload as far throughout it as possible. When it later activates, it encrypts entire file systems in a manner that is impossible to undo without knowing the decryption key. Attackers then usually offer to decrypt the file systems for a ransom, typically paid in cryptocurrency, but in some cases no ransom demand is ever transmitted.
The FBI has urged victims not to pay ransoms, which don’t guarantee that the operators behind the attack will actually release the data and incentivise future attacks. But it also wants victims to report when they do so that the agency can build more detailed profiles of cybercrime organisations demanding them.
The FBI expects that trend to continue.
Those losses can far outstrip the extortion demands. Hackers that kneecapped the Baltimore city government for weeks in May 2019 demanded just $US102,000 ($148,111) in bitcoin, but destroyed large amounts of data and cost an estimated $US18.2 ($26) million in recovery costs and lost or delayed revenue.
According to a recent report by security firm Emsisoft, there have been at least 948 documented ransomware attacks in 2019. That includes 103 on “government entities,” 759 on healthcare providers, and 86 on educational institutions. Emsisoft described the ongoing series of attacks as an “unprecedented and unrelenting barrage” resulting in potentially serious situations like interruption of emergency services and other emergency care, loss of medical records, surveillance systems going offline, and police unable to access IT systems.
That’s not counting things like city operations of all kinds, from tax payment systems and driver’s licence renewals, grinding to a halt in some cases. State governments have also been disrupted, as in the case of an August 2019 attack on at least 23 agencies in Texas.
Attackers have recently begun extorting targets with the threat of releasing their data to the internet. In the Allied Universal attack using Maze ransomware, for example, the operators involved demanded $US2.3 ($3) million in bitcoin and published 700 megabytes of the security firm’s files when they didn’t pay up. In the Pensacola attack, Maze operators threatened to do the same with municipal government data.
A website allegedly run by Maze operators has been posting data that appears to be stolen from several corporations, including an Ann Arbor, Michigan food market that wrote a blog post explaining that it had not paid off the “cyber-terrorists” involved.
“The switch to “˜double whammy’ attacks in which data is exfiltrated prior to being encrypted is likely simply an experiment to see whether this approach is more profitable than traditional encryption-only attacks,” Emsisoft spokesman Brett Callow told Gizmodo via email. “In other words, bad actors believe that the additional leverage may make it more likely that victims will pay. Whether this proves to be the case remains to be seen. Will companies really pay on the basis of a pinky-promise made by criminals not to release data?”
Emsisoft wasn’t able to come up with a reliable estimate of the costs, but it did note that “organisations’ existing security weaknesses and the development of increasingly sophisticated attack mechanisms specifically designed to exploit those weaknesses” had created a “perfect storm” throughout the year.
It added that the incidents are exposing poor IT practices on the state and local level and at many large institutions, with problems ranging from a lack of uniform standards to underfunding. A ProPublica report in August emphasised that some cities and companies have relied on insurance reimbursements for ransom payments as a cheaper alternative to losing revenue and hiring expensive consultants.
Bret Padres, CEO of security firm Crypsis, told ProPublica that there’s “really good money in ransomware” not only for the attackers, but recovery experts brought in after the fact and insurance companies that profit from selling coverage against extortion threats. Padres told the site that it’s a “vicious circle” and a “hard cycle to break because everyone involved profits: We do, the insurance carriers do, the attackers do.”