Security researchers said Wednesday that at least 500,000 home and small business routers in up to 54 countries are infected with a new breed of malware called VPNFilter, a prior version of which wreaked havoc across Ukraine.
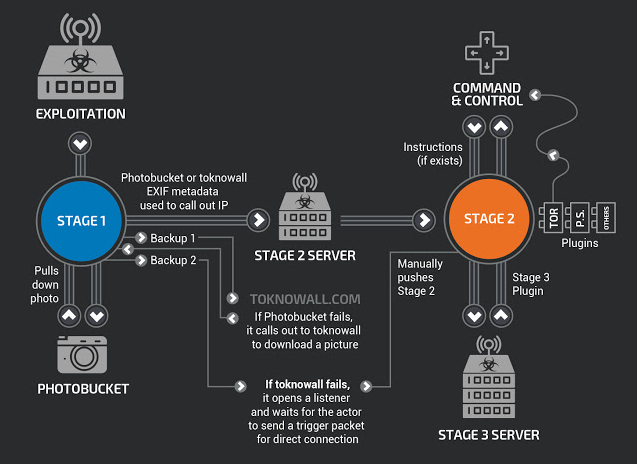
Cisco’s Talos cybersecurity unit reports that VPNFilter is likely the product of an advanced threat with nation-state backing and while it may have been deployed as spyware, its creators had multiple aims. VPNFilter’s stage 2 malware includes a “self-destruct” feature which, when activated, overrides critical portions of the infected device’s firmware, effectively bricking it. (“Stage 2” refers to malware installed after initial infection.)
Talos assesses with high confidence that the self-destruct feature could be triggered on nearly every device infected. Stage 2, which does not survive a reboot of the device, also includes the bulk of VPNFilter’s intelligence gathering tools, enabling command execution as well as data collection and exfiltration.
“The known devices affected by VPNFilter are Linksys, MikroTik, NETGEAR and TP-Link networking equipment in the small and home office (SOHO) space, as well at QNAP network-attached storage (NAS) devices,” Talos said in the report. The malware is not known to have infected other types of routers, though they may be susceptible, and it appears to avoid IoT devices, which purge malware typically when rebooted.
Graphic: Talos
But wait! There’s more:
VPNFilter also has a stage 3, which adds a packet-sniffing application allowing attackers to monitor internet traffic and intercept website credentials, as well as a module that enables the malware to communicate over the Tor onion network. Talos also suspects there may be other plugins available VPNFilter, which the researchers have simply yet to uncover.
The hackers responsible may also network the infected devices to create “hop points” and conceal their origin(s) before carrying out other attacks. (Hence the name.)
“Advanced threat actors, including nation-states, will try to make attribution of their cyber activities extremely difficult, unless it is in their interest for it to be openly known that they conducted a specific act,” Talos said. “To this end, advanced threat actors use multiple techniques, including co-opting infrastructure owned by someone else to conduct their operations.”
Talos added that defending against VPNFilter is “extremely difficult” because there’s little or no security between most home and small business routers and the internet, not to mention zero anti-malware capabilities. “This challenge is augmented by the fact that most of the affected devices have publicly known vulnerabilities which are not convenient for the average user to patch,” Talos said.
Empow security founder Avi Chesla told Gizmodo that the probability of infection is likely highest when users fail to change a router’s default username and password – though hackers have also been known to hijack firmware update channels. In addition to spying and destroying the routers, Chelsa warned about the potential of the devices being networked to launch denial-of-service attacks, redirect users to malicious websites, or even launch ransomware (which is sometimes used as a smokescreen to more destructive ends).
“It’s very hard to prevent because although the vulnerability was known, it is harder to patch routers,” said Chelsa, the router-update process being outside the scope of an average user’s skill. (It’s for this exact reason that many intelligence agencies prefer targeting routers over Macs and PCs.) The impact can be mitigated, however, by finding and terminating the command and control channel used by this malware, he said.
The researchers Talos offered a handful of recommendations as well, to both users and service providers:
- Users of [small office/home office] (SOHO) routers and/or NAS devices reset them to factory defaults and reboot them in order to remove the potentially destructive, non-persistent stage 2 and stage 3 malware.
- Internet service providers that provide SOHO routers to their users reboot the routers on their customers’ behalf.
- If you have any of the devices known or suspected to be affected by this threat, it is extremely important that you work with the manufacturer to ensure that your device is up to date with the latest patch versions. If not, you should apply the updated patches immediately.
- ISPs work aggressively with their customers to ensure their devices are patched to the most recent firmware/software versions.
Due to the potential for destructive action by the threat actor, we recommend out of an abundance of caution that these actions be taken for all SOHO or NAS devices, whether or not they are known to be affected by this threat.
