Employing sophisticated scams involving social engineering, email phishing, and the harvesting of employee passwords, attackers have pilfered millions of dollars from some of the world largest corporations – all while bypassing traditional hacking safeguards by simply avoiding the use of malware.
Photo: Getty
A new report from IBM Security sheds light on ongoing campaigns being waged by “cyber con artists” employing a known scam called Business Email Compromise (BEC). These attacks take on many forms, but typically include fraud involving fake invoices, impersonation of high-ranking corporate officers, and the targeting of accounting or human resources staff to gather sensitive financial information, such as tax statements.
The threats tracked by IBM’s global threat intelligence service, known as X-Force (insert Marvel Comics joke here), began by harvesting mass amounts of business user credentials, which in studied incidents enabled attackers to impersonate corporate officers authorised to make large fund transfers.
The compromised accounts were gathered largely using traditional phishing techniques.
In one case, an official-looking email sent to hundreds of corporate contacts appeared to contain a link to a business document. The targets were directed to a fake “DocuSign” website where they were first asked to log in using their email credentials. The attack targeted primarily personnel working in the company’s accounts payable department, the report says.
A key defence against this form of credential harvesting is implementing multi-factor authentication.
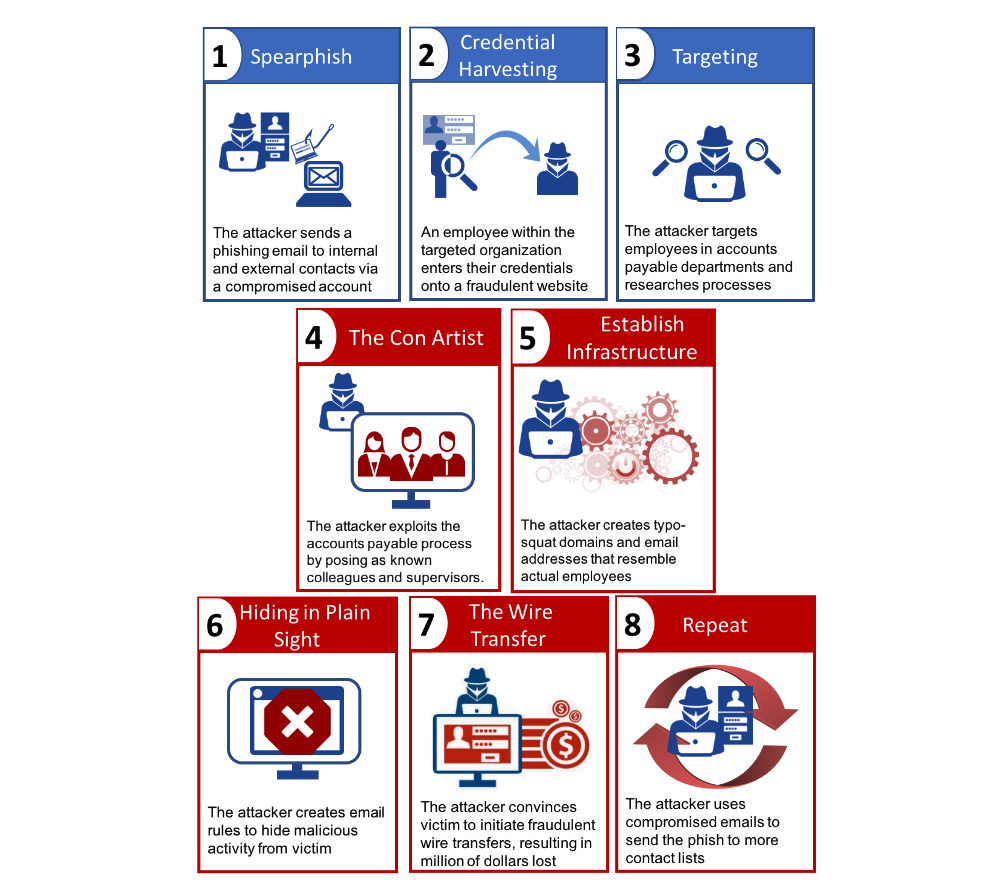
A Business Email Compromise attack relies heavily on social engineer tactics as opposed to network penetration. (Image: IBM Security)
“To successfully scam companies without special tools or malware, the attackers used sophisticated social engineering tactics that prey on flaws in common accounts payable processes,” IBM reports, such as impersonating vendors that have established relationships with the target. This deception would require some in-depth knowledge of the targeted company’s business ties.
“The attacker’s thoroughness during reconnaissance and while financial conversations took place has involved such actions as impersonating victims, finding and spoofing internal documents needed to make legitimate wire transfers, and setting up multiple domains and emails to pose as higher-level authorities,” the report says.
Because the thefts often involved millions of dollars, the threat groups would go as far as creating shell companies, typically with corresponding bank accounts in Hong Kong or China, as consumer accounts involved in transfers of that size typically warrant additional scrutiny, the report notes.
IBM asserts that the attackers assessed in its research likely originate in Nigeria, though attribution is always tricky. Sophisticated threats often mask their locations by staging attacks from compromised servers in foreign countries.
Business Email Compromise attacks are a growing threat. In December, the cyber defence firm TrendMicro estimated BEC would lead to more than $US9 billion ($11 billion) in global losses in 2018, based on a flat growth scenario. In a May 2017 advisory, the Federal Bureau of Investigation claimed BEC had grown into a $US5.3 billion ($7 billion) global industry and reported a 2370 per cent increase in losses between January 2015 and December 2016.
Read the full IBM Security report here.
