This weekend, a security consultant detailed what he believed were serious vulnerabilities in Uber’s software – and his disbelief that the company’s bug bounty program refused to pay him for his research. Unfortunately, it’s a story without heroes.
The researcher, Gregory Perry, made his displeasure with Uber known in a Medium post (“How I Got Paid $US0 ($0) From the Uber Security Bug Bounty“) on Sunday, listing four issues he had discovered with the legally embroiled ride-sharing company’s software. Among these was the discovery that Uber’s implementation of OAuth – an open protocol used to securely log-in users to pages and services — allowed some authentication tokens to never expire. Despite the promise of a minimum payout of $US500 ($648) for each discovered bug, Perry claims he was never paid by Uber primarily because the company claimed it was already aware of the bugs he reported.
“This sounds like really bad security on Uber’s part,” Aaron Parecki, author of OAuth 2.0 Simplified and consultant on the protocol, told Gizmodo over email. “OAuth recommends that access token lifetime is very short, only as long as necessary depending on the risk associated with the token leaking. Examples given are minutes to hours.” He further commented that an extension for handling these issues was published back in 2013.
Naturally, the perception that a distrusted company stiffed a well-meaning researcher out of a couple hundred bucks sparked a firestorm on Twitter and hacker-friendly forums. If accurate, this wouldn’t be the first or even close to the highest-profile example of Uber failing to protect user data. Hackers exposed the data of 57 million users back in 2016, which the company only admitted earlier this month.
How to NOT win bug bounties:
1. Treat the people triaging reports like shit:https://t.co/b0oHRvTV6vhttps://t.co/NsgLQoCD4K
2. Angrily write a blog post shaming the company because you couldn’t find any valid, non duplicate issues:https://t.co/0OrcDZsXBX— shubs (@infosec_au) December 24, 2017
With every reason to distrust Uber, a number of security researchers stood with the company’s handling of this incident, however, citing the non-critical nature of the reported bugs, the likeliness that such bugs truly were known to Uber prior to these reports, and most of all, Perry’s conduct in being rebuffed.
Responses to Perry’s reports on disclosure platform HackerOne from Uber’s security team were detailed and professional — including the OAuth issue, which the team explained was a result of a legacy system that was being phased out — while Perry’s were combative (“Cute. Big surprise,” he wrote after being told one such bug was known.) This culminated in an attack impugning the credentials of Uber’s security program manager
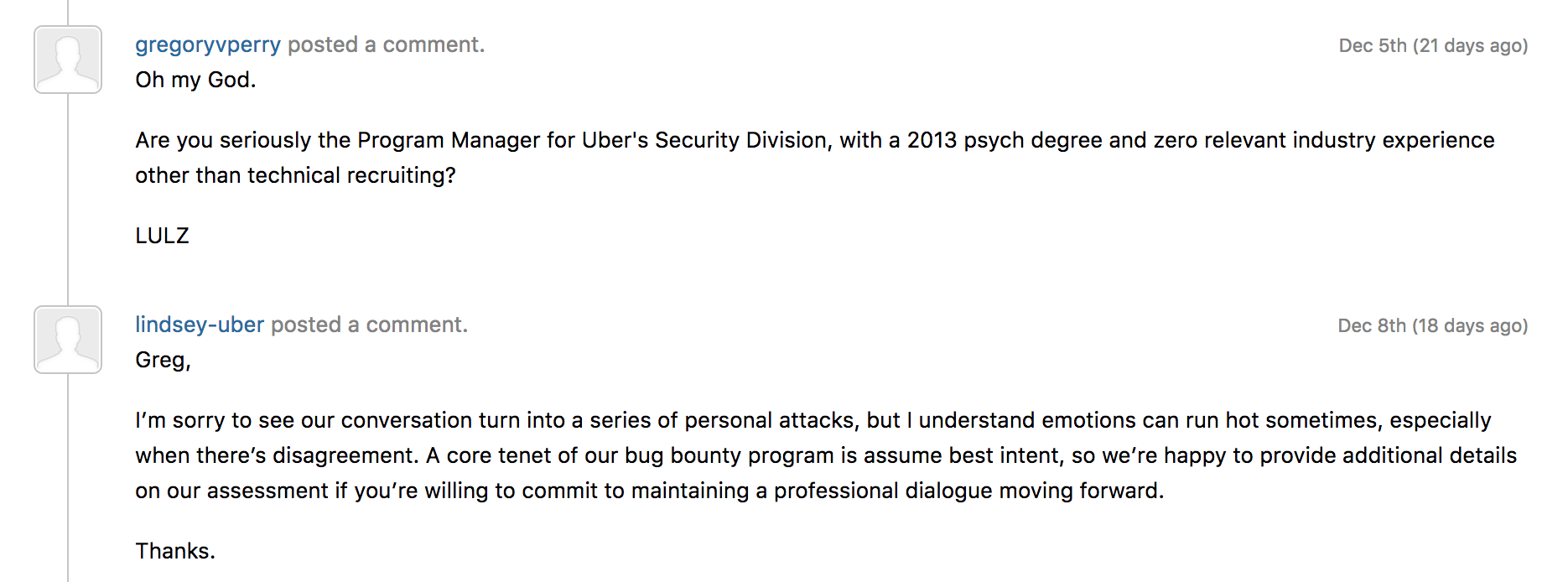
HackerOne’s founder commented on this exchange earlier today on Twitter, stating that “this community leaves no tolerance for personal harassment. Brilliant Jerks are invited to apply their talents elsewhere.”
3) A finder will never face punitive action for professional debate, dialog, or dissent. Reasonable people will disagree.
But this community leaves no tolerance for personal harrassment. Brilliant Jerks are invited to apply their talents elsewhere.
Be excellent to each other.
— Alex Rice (@senorarroz) December 26, 2017
Uber may have handled this dustup responsibly, but it remains a company with a legacy of less-than-admirable business practices that have engendered serious distrust from the public. Perry, on the other hand, is just a garden-variety jerk. Still, the uproar caused by Perry’s post undermines the utility of bug bounty programs – the preferable alternative to exploits being sold to malicious parties instead of the companies (and customers) they endanger.
