Last week, Twitter’s security team purged nearly 90,000 fake accounts after outside researchers discovered a massive botnet peddling links to fake “dating” and “romance” services. The accounts had already generated more than 8.5 million posts aimed at driving users to a variety of subscription-based scam websites with promises of — you guessed it — hot internet sex.
Screencap: ZeroFOX
The accounts were first identified by ZeroFOX, a Baltimore-based security firm that specialises in social-media threat detection. The researchers dubbed the botnet “SIREN” after sea-nymphs described in Greek mythology as half-bird half-woman creatures whose sweet songs often lured horny, drunken sailors to their rocky deaths — presumably for the purpose of feasting upon their vitamin-deficient corpses.
ZeroFOX’s research into SIREN offers a rare glimpse into how efficient scammers have become at bypassing Twitter’s anti-spam techniques. Further, it demonstrates how effective these types of botnets can be: The since-deleted accounts collectively generated upwards of 30 million clicks — easily trackable since the links all used Google’s URL shortening service.
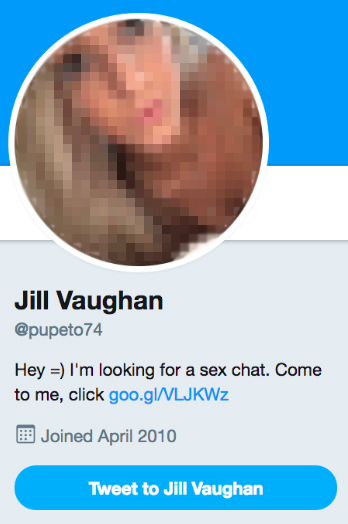
The 90,000 accounts were all created using roughly the same formula: A profile picture of a stereotypically attractive young woman whose tweets included sexually suggestive, poorly written remarks that invite users to “meet” with them for a “sex chat”. Millions of users apparently fell for the ruse and, presumably, a small fraction of went on to provide their payment card information to the pornographic websites they were lured to.
“The accounts either engage directly with a target by quoting one of their tweets or attracting targets to the payload visible on their profile bio or pinned tweet,” ZeroFOX reports. Roughly 20 per cent of the accounts lay dormant for a year before sending their first tweets, an effort to evade Twitter’s anti-spam detection.
Here’s just a brief sample of the hilariously bad tweets generated by these obviously fake accounts:
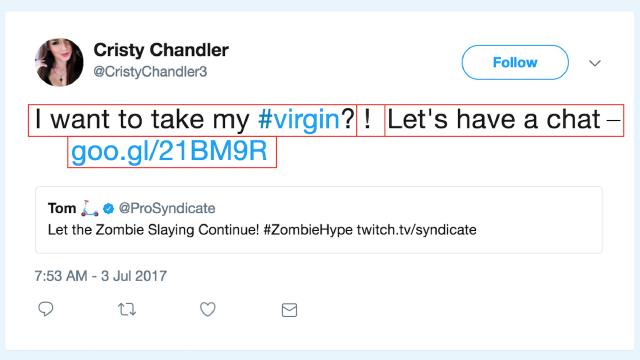
- “I want to #fondle me?”
- “I want to take my #virgin?”
- “Came home from training, tired wildly?”
- “Meow, I want to have sex.”
- “Boys like you, my figure?”
- “Want a vulgar, young man?”
The tweets further included links to affiliate programs — web pages that typically redirect users to other adult websites. Members of these programs, which traditionally rely heavily on spam, receive payouts based on the amount of traffic they send to subscription-based porn and so-called “adult dating” websites. Likewise, many of the “dating” websites are themselves scams, chiefly comprised of fake female profiles which encourage visitors to sign up for paid subscriptions with promises of lame cybersex and nudes. (PSA: There are literally no women on the internet that want to have sex with you.)
According to ZeroFOX, two out of five of the domains tweeted by the SIREN botnet are associated with a company called Deniro Marketing. Deniro Marketing was identified earlier this year by noted security researcher Brian Krebs as being tied to a “porn-pimping spam botnet“. (Krebs also filed a report Monday regarding ZeroFOX’s discovery.) The company reportedly settled a lawsuit in 2010 for an undisclosed sum after being accused of operating an online dating service overrun with fake profiles of young women.
A Deniro Marketing employee who answered the phone at its California headquarters on Monday said that no one was available to respond to inquiries from reporters.
While it seems unlikely that Deniro Marketing created the fake accounts itself, it may have contracted a third party — likely located somewhere in Russia or Eastern Europe — to spread the links for them. A “large chunk” of the accounts’ self-declared languages were Russian, ZeroFOX reports, and approximately 12.5 per cent of the bot names contained letters from the Cyrillic alphabet.
“To our knowledge, the botnet is one of the largest malicious campaigns ever recorded on a social network,” ZeroFox concludes. Luckily, none of the links tweeted by the SIREN botnet appear to contain malware, nor were any associated with phishing attempts. But with more than 30 million clicks, the discovery reveals what a threat such an operation could be if the goal were shifted slightly to include, for example, the spread of ransomware.
Twitter did not immediately respond to a request for comment.
[ZeroFOX]