In an impressive bit of cyber-sleuthing, security researchers have discovered that a nasty piece of malware was being tested by a Russian-speaking hacker group, and it was using the comment section of Britney Spears’s Instagram as a way to call home.
Photo: Getty
Turla is a hacking group that specialises in using malware for the purposes of espionage. The fancy name for the collective is an advanced persistent threat group. Researchers from ESET report that they have recently discovered a backdoor trojan that appears to have been created by the group, but it hasn’t been deployed on a wide scale yet.
The malware itself isn’t particularly mindblowing. It uses a Firefox extension to create a backdoor that gives an attacker complete access to a target’s computer. The researchers believe it could be an adaptation of the Pacifier APT that was spread via Microsoft Word docs back in 2016.
Turla is known to use “watering holes” or compromised sites that their targets are likely to visit for distributing its malware. This particular trojan was discovered on a Swiss security company’s website. Visitors to the site would be asked to install the extension with the benign name “HTML5 Encoder”.
But the real innovation, in this case, is the hackers using social media to contact their malware’s command and control (C&C) servers. These servers send instructions and act as a repository for stolen information. Using an encoded coded comment on Britney Spears Instagram post, the malware could find out what URL to use to meet up with the server without actually including that information in the code of the malware itself.
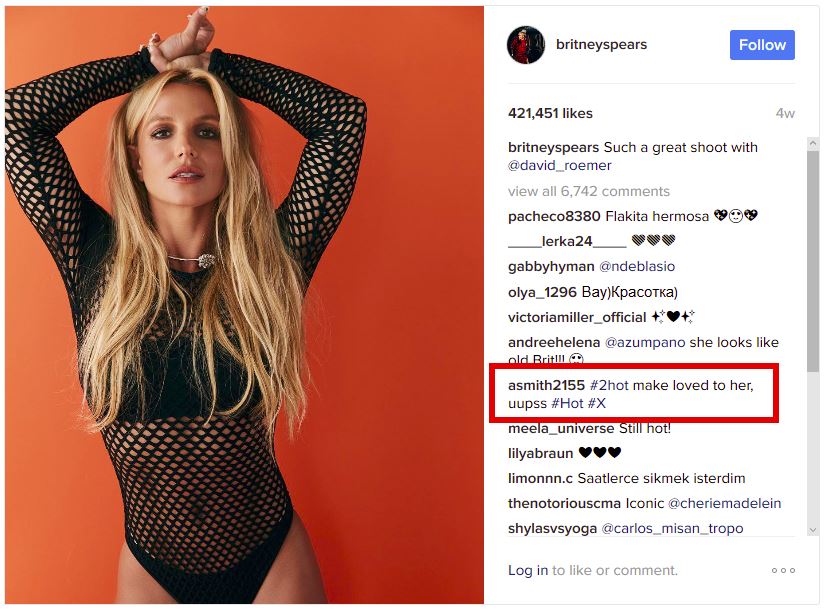
The smoking gun comment
The malware was directed to scroll through the comments on Spears’s photos and search for one that had a specific hash value. As you can see, the comment in question isn’t exactly a normal post, but it passes as basic spam and no one would give it a second thought. However if you copy and paste it, you’ll find that it uses the Unicode character 200d and it looks like this: smith2155< 200d >#2hot ma< 200d >ke lovei< 200d >d to < 200d >her,< 200d >uupss< 200d >#Hot< 200d >#X. When the malware finds the comment it was told to look for, it converts it into this Bitly link: http://bit.ly/2kdhuHX. The shortened link resolves to a site that’s known to be a Turla watering hole. This is a stealthy way of making sure that the C&C can be changed without having to change the malware. If the attackers want to create a new meetup, they just have to delete the comment and put in a new one with the same hash value.
ESET has been in contact with Firefox’s developers and they’re currently working on a fix so that the extension won’t work any more. And Miss Spears will probably never know that her photo came close to being used in international espionage.
