I’ve never really been crazy about proximity keys, mostly because I’m a scatter-brained fool. The overall car industry loves them, though, and most new cars use these types of keyless entry systems. A team of Chinese researchers have figured out a very clever and cheap way to hack the passive keyless entry system and actually drive off in people’s cars.
The team that figured this out calls themselves Unicorn Team, and consists of three researchers, Yingtao Zeng, Qing Yang, and Jun Li. They presented their findings at the HITB conference in Amsterdam.
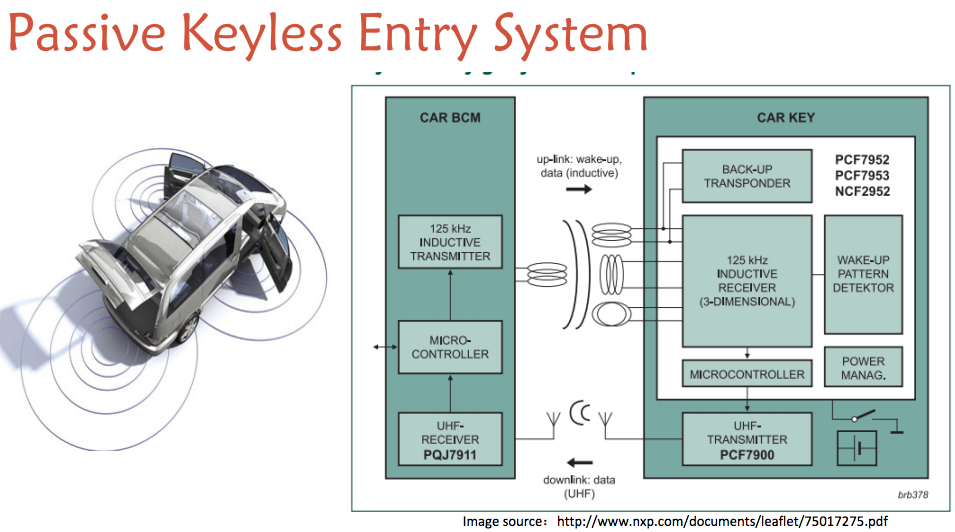
From the team’s slide deck.
Essentially, the way most keyless entry systems work is that the key fob, nestled in the warm, welcoming confines of your pocket or purse, sends radio signals to the car, which responds, and the tiny, fast data-conversation between the two results in the car unlocking and being ready to drive.
This only works if the key is very close to the car; hence the name ‘proximity’ key. What these researchers have managed to do, in essence, is to fool the car into thinking the key is very close by, even when it’s not.
The way they do this is via a pair of radio devices: one is near the key, capturing the radio signals, and the other can be up to 1000 feet away, receiving the signals from the key fob and sending them to the car.
That means a pair of dishonest people could get access to your car and even drive it off (once they turn it off, though, they won’t be able to re-start it) by having someone just near the proximity key, and another near the car. They made a little video dramatizing the excitement:
Effectively, they have built a range-extender for the proximity key. Earlier versions of this same concept essentially just recorded the radio signal, transmitted it, and played it back. These earlier attempts used equipment that cost thousands of dollars (later down to hundreds), and had a range less than a third of the range of this new hack.
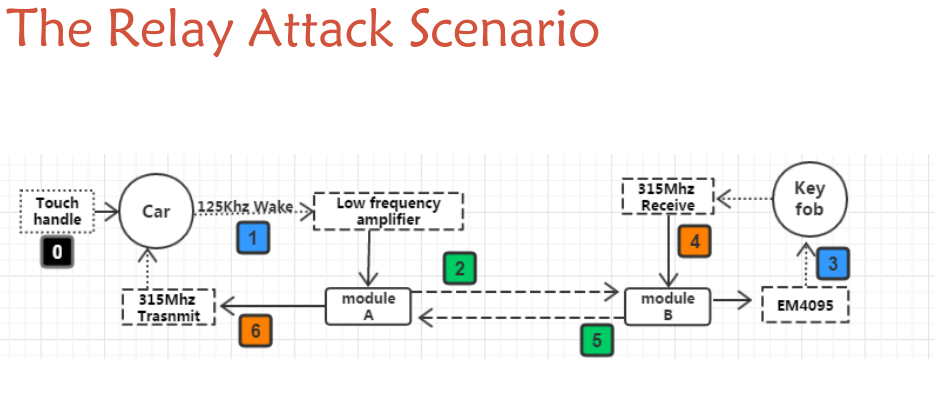
What makes Unicorn Team’s hack so amazing is that they have reverse-engineered the radio signal from the proximity key, and are able to convert that signal to data, and then re-send that data at a much lower frequency, which allows for the far greater signal range.
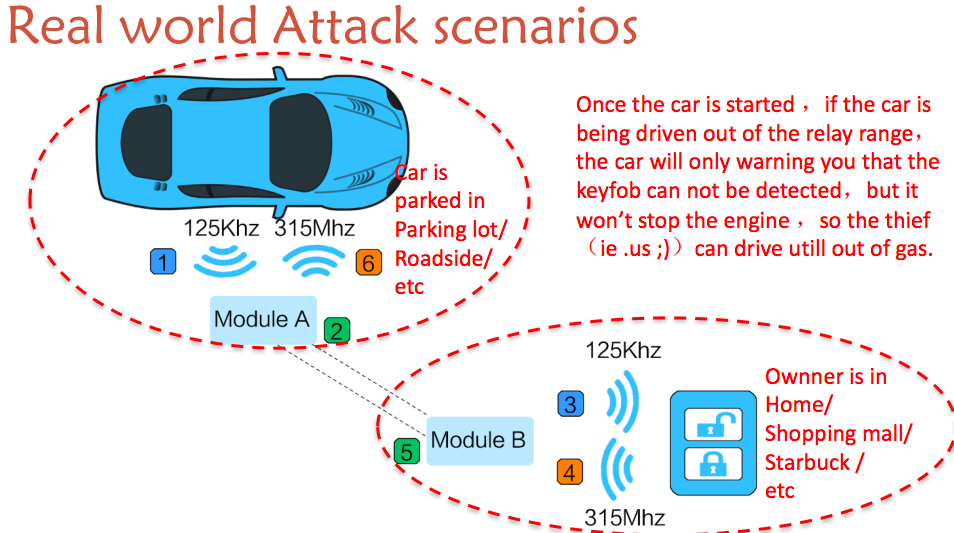
The team has suggested to manufacturers that a way to help prevent these sorts of signal-relay attacks would be to reduce the amount of time it takes before the car’s lock system times out, though the nature of such passive-key systems is inherently insecure.
There are solutions, though! Keep your key in something like a Faraday Cage would keep the signals from being detectable, like your refrigerator or microwave. You carry a microwave around with you anyway, right? Just put your keys in there!
(Thanks, Charles!)
