After searching through the Ashley Madison database and private email last week, I reported that there might be roughly 12,000 real women active on Ashley Madison. Now, after looking at the company’s source code, it’s clear that I arrived at that low number based in part on a misunderstanding of the evidence. Equally clear is new evidence that Ashley Madison created more than 70,000 female bots to send male users millions of fake messages, hoping to create the illusion of a vast playland of available women.
Today Ashley Madison released a statement saying that I couldn’t have figured out how many active women are on the site based on the data dump. The company is right about that. It may still be true that a relatively small number of women are active on Ashley Madison, but the evidence that I thought supported my claims means something else entirely — more on that below.
What I have learned from examining the site’s the source code is that Ashley Madison’s army of fembots appears to have been a sophisticated, deliberate, and lucrative fraud. The code tells the story of a company trying to weave the illusion that women on the site were plentiful and eager. Whatever the total number of real, active female Ashley Madison users is, the company was clearly on a desperate quest to design legions of fake women to interact with the men on the site.
The Missing Data and the Bots
The Ashley Madison source code comes from the second dump released by Impact Team — at 20 gigabytes compressed, it was about twice the size of the first. Though partly corrupted, it did hold hundreds of readable company emails that revealed the company was paying people to create fake women’s profiles and to chat with men on the site. It also contained multiple git repositories, or containers for source code, that appear to go back to mid-2010.
The first thing I learned when I looked at the code was that the database Impact Team released on August 18, and on which I based my reporting about the number of active female users, was just a tiny portion of the actual member data collected by Ashley Madison. The code makes references to 550 data tables, but there are only 4 tables in the data from Impact Team. That radically changes the picture of what we’re actually seeing in the database.
When I first looked over the data, I wrongly assumed that I had all or most of the tables. As I wrote last week, I came across three columns in one of those tables called “bc_email_last_time,” “bc_chat_last_time,” and “email_reply_last_time.” After consulting with two analysts, and determining that these columns were the only ones with names typically used to track user activity, I concluded that the datestamps in those columns referred to the last time people checked their Ashley Madison messages, or tried to start a chat. And when I saw the radical disparity between numbers of men with a datestamp and the number of women, I interpreted it to mean that men were emailing a lot with bots, and women barely ever emailed anyone at all.
But I was wrong. It’s a lot weirder than that. Those columns in the data don’t record human activity at all. They record the last time a bot — or “engager” in Ashley Madison’s internal parlance — emailed or chatted with a member of the site.
What that means is that we have absolutely no data recording human activity at all in the Ashley Madison database dump from Impact Team. All we can see is when fake humans contacted real ones. In other words, the dramatic discrepancy between men and women is entirely because Ashley Madison’s software developers trained their bots to talk almost exclusively to men.
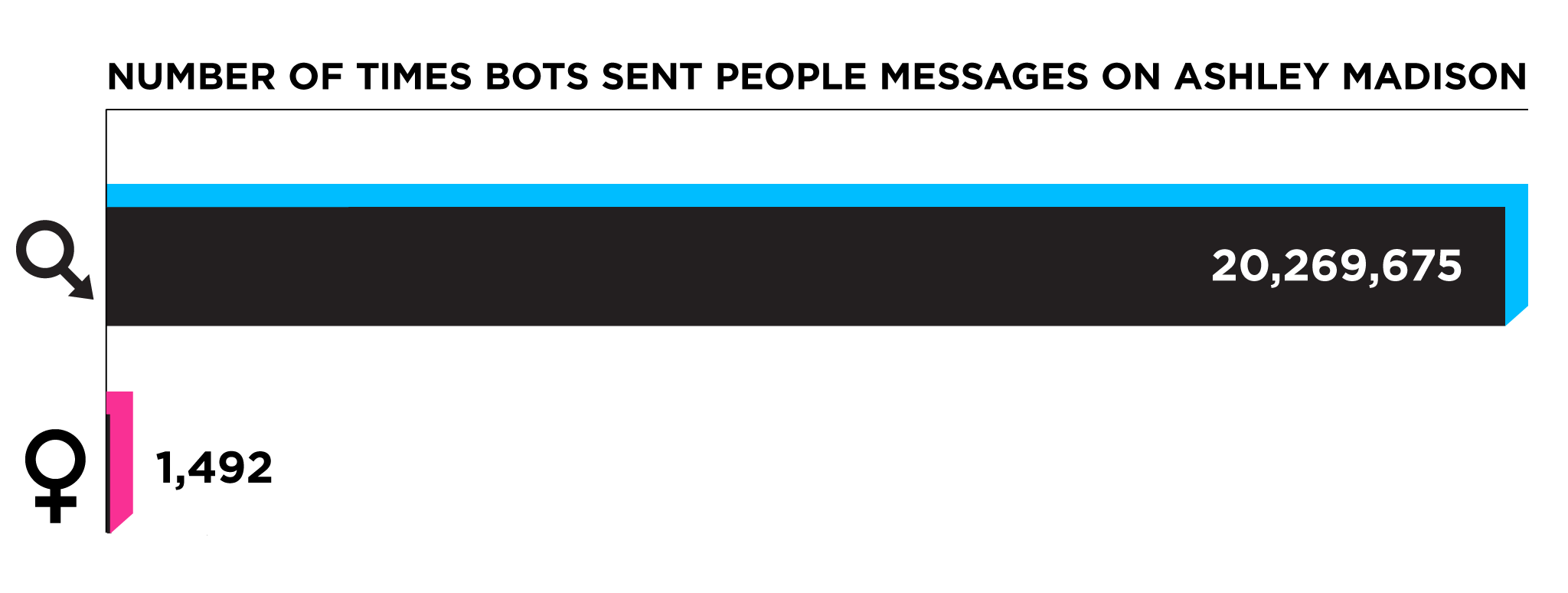
Two intrepid researchers came forward to tip me off to what those columns actually measured. Software developer Jake Perkowski and pseudonymous Gizmodo commenter Mr. Falcon had both pored over the code and realised that when bots called “engagers” talked to humans, they were programmed to make a note of it in the database under fields called “bc_chat_last_time,” “reply_email_last_time,” “or bc_email_last_time.” Once I’d checked the sections of code they pointed to, the evidence was undeniable. Those columns had been populated by bots, obediently checking in every time they talked to a human male.
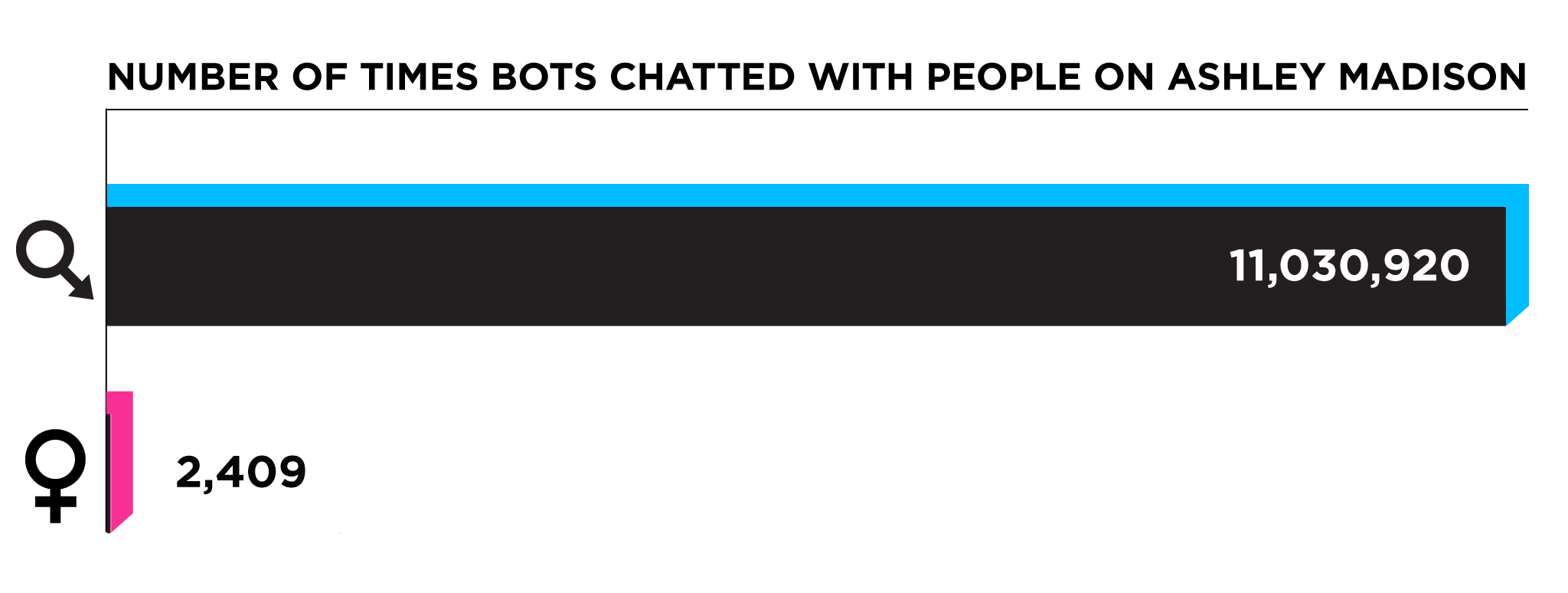
Perkowski also pointed me to a column in the database called ishost. When ishost was set to 1, he said, it meant that the member was actually a bot. A quick search of the code revealed that indeed bots were using accounts with the value ishost=1. So I decided to delve more into what else these host accounts held.

Out of 70,572 hosts, 70,529 were female and only 43 were male. So we can say for sure that roughly zero per cent of bots on Ashley Madison are male. The bots also tended to have ashleymadison.com email addresses, though other popular addresses included things like passthecake@hotmail.com, kimmakesprofiles@hotmail.com, and digital-romeo@hotmail.com. And finally, tens of thousands of the bots had IP addresses that suggested the accounts had been made by people working at the Ashley Madison office.
But where can we find human activity in the Impact Team dump? Apparently, nowhere. Looking at the code, there appear to be several database tables where the system keeps track of when humans chat or message with other humans. It also seems that Ashley Madison even keeps records of what each member says to the other in chat sessions. Had the Impact Team been more nosy, or had more time to dump the data, we might be looking at extremely detailed information on what humans said to each other as they flirted and planned their hookups.
So much for Ashley Madison’s guarantee that they will keep your affair hushed up. Right now, the company has reams of incredibly incriminating personal information about everything its human users are doing and saying.
But in the database dump from Impact Team, all we can see is the ample evidence that male users were contacted by bots pretty much constantly. Those data fields tell us that 20 million men out of 31 million received bot mail, and about 11 million of them were chatted up by an automated “engager.” And in the code, I discovered that for many members, these robo-encounters could come roughly every few minutes. At last, I was able to see how a group of engineers tried to create bots that would make men feel like they were in a world packed with eager, available women.
How to Snare Millions of Men with Web Bots
It’s not easy to sort through thousands of lines of code, but two things can make it faster. One is a simple but powerful search program called grep that can search text for any phrase you like. The other is a habit that engineers have of writing comments about what they’re doing in the code. Armed with grep, I could look for key phrases in both comments and the code itself.
I knew from the company emails that the engineers and managers used certain terms for the bots, including “hosts” and “engagers.” Perhaps one of the most poignant parts of reading the engineers’ comments in the code was when I uncovered a set of descriptions for how the engager bots should act. I found these in a database devoted to engager activity. Here are a few of them:
host bot mother creates engagers
birth has been given! let the engager find itself a man!
randomizing start time so engagers don’t all pop up at the same time
for every single state that has guest males, we want to have a chat engager
These comments describe a bot being born and immediately turning to its one purpose in life: finding a man. Then the developer notes that it’s important that “engagers don’t pop up at the same time.” The engager bots are basically pieces of software. They operate by inhabiting, as a demon might, previously existing fake profiles that the company calls “Angels” — these are the profiles that Ashley Madison CEO Noel Biderman was pushing his people to create at scale in internal company emails. The Angels, also called “hosts” by the company’s engineers, lay dormant until a bot animates them and uses them like a skin to contact a male user. Which is why the engineers sought ways to prevent them from all grabbing the same identity at the same time. Basically, they look a lot less fake if there aren’t a zillion bot clones running around chatting men up. And finally, we learn that one of the rules was that every state with non-paying “guest” males — from Nunavut to California — should have a chat engager.
Of course, things didn’t always go as planned. In a patch, or edit, to the code, I saw this comment: “Stopped engaging gaymen.” That made me laugh. I imagined a frustrated developer, getting complaints from gay men who kept being assaulted by female chat bots looking for heterosexual love.
Based on what I’ve seen in the code, the chat bots were fairly annoying. First of all, they weren’t exactly smart. Here’s a verbatim list, taken directly from the code, of the random messages that the chat bot was programmed to spew — probably the repeats are in there to make it more likely that the bot would say them:
‘hi’,
‘hi’,
‘hi’,
‘hi (s)’,
‘hi there’,
‘how are you?’,
‘hey’,
‘Hey’,
‘hey there’,
‘hey there’,
‘Hey there’,
‘u busy?’,
‘you there?’,
‘any body home?’,
‘Hi’,
‘Hi’,
‘Hi’,
‘hows it going?’,
‘chat?’,
‘how r u?’,
‘anybody home? lol’,
‘hello’,
‘hello’,
‘Hello’,
‘hello?’,
‘whats up?’,
‘so what brings you here?’,
‘oh hello’,
‘free to chat??’,
Once the man struck up a conversation, the bot would say things like this:
Hmmmm, when I was younger I used to sleep with my friend’s boyfriends. I guess old habits die hard although I could never sleep with their husbands.
I’m sexy, discreet, and always up for kinky chat. Would also meet up in person if we get to know each other and think there might be a good connection. Does this sound intriguing?”
It’s unclear what else the engager would say — either the bots really are this simple, or further chat phrases weren’t in the code. Most likely, based on what I saw from other bot code, the bot would urge the man to pay credits to talk further.
Mr. Falcon pointed out that there’s actually a special bot service, called “RunChatBotXmppGuarentee.service.php,” apparently designed just for interactions with customers who paid the premium $US250 for a “guaranteed affair.” When I checked the code, I found Mr. Falcon was right. It appears that this bot would chat up the man, urge him to pay credits, and then pass him along to what’s called an “affiliate.” Likely the affiliate is a third party that provides a real person for the man to chat with. It might also be connecting him to an escort service.
Earlier this year, one Ashley Madison engineer spent a couple of days mocking up a possible system for paying actual human women for engaging the men. The code calculates a “FemaleValue” (percentage credited to the woman’s account) based on “MaleProfit” (amount the man pays to Ashley Madison). If the woman engages the man within 20 to 30 minutes of the time he buys credits, she’ll be credited with 5 per cent of the profit. It doesn’t appear that this system was deployed, but it was obviously something Ashley Madison developers were thinking about.
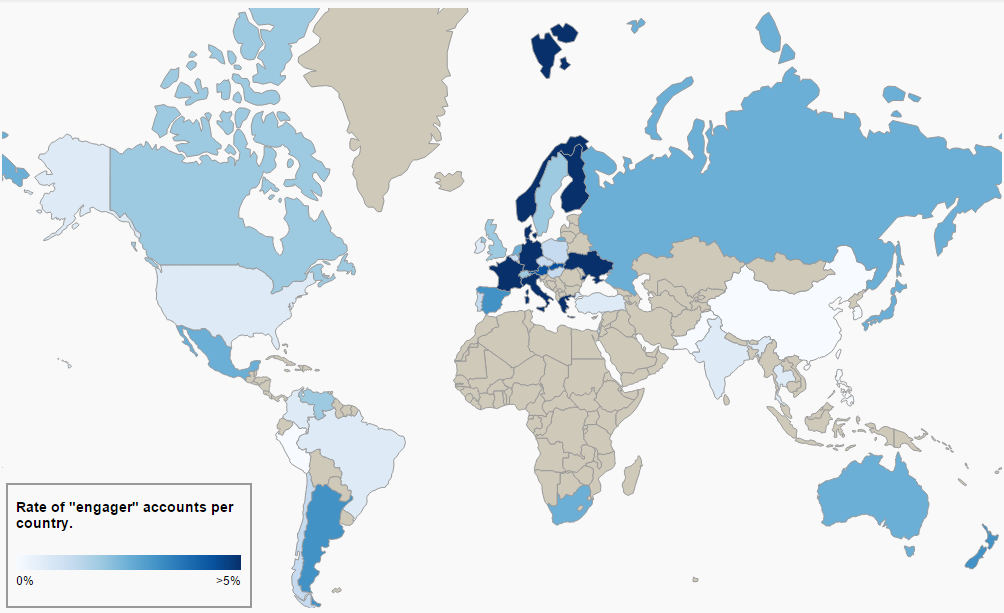
Map via Jake Perkowski
We know from company emails that management constantly struggled to find people to create fake accounts in languages other than English. Bots needed to speak 31 different languages, and they chatted and sent messages to people in roughly 50 countries and 1,500 states or provinces. In the map above, Perkowski has visualized “the rate of engager accounts to total female accounts per country.” The darker the blue, the more ubiquitous robots are in your Ashley Madison dating pool. No matter where you are in the world, Ashley Madison probably has a bot that can say “anybody home? lol” in your native language.
Perhaps because of the company’s international focus, you can see ripples of geopolitical events in the code. I found evidence that a developer updated the system in May to change the handling of payments in Crimea. No doubt responding to the Russian invasion of that region, he changed the payment system language from Ukrainian to Russian. In another comment, a developer noted, “south african engagers can only engage pnums [members] of same race.”
Ashley Madison aspired to be a global network of people breaking the bonds of monogamy in the name of YOLO. Instead, it was mostly a collection straight men talking to extremely busy bots who bombarded them with messages asking for money. I found a set of email templates called “mistress” which were sent out to urge men to spend money on Mistress Day, a pre-Valentines holiday on February 13. Ashley Madison CEO Noel Biderman did a huge publicity push for the holiday in 2014, doing interviews about it in the media and blasting out emails urging all members to buy more credits so they can find a mistress in time for the day.
Those email blasts were another way the bots hassled Ashley Madison’s straight men. One engineer comments in the code that bot mail blasts for new members are sent to straight men on Monday, Wednesday and Friday; but they’re only sent to men seeking men on Tuesdays, and women seeking women on Thursday.
The engagers are so annoying that developers had to write special exceptions to exclude their own bots from being nuked in spam sweeps. They also exclude several IP addresses in India and the Philippines, which suggests that they may have had a lot of people operating their host accounts in those regions.
The Humans
After I published my first article about Ashley Madison data, I got a several dozen emails from women and men who told me their stories about using the service. Some agreed with my assessment that the place is a sexbot farm. But many women described how they’d enjoyed the service for years, and men talked in glowing terms about all the amazing women they’d met, including some who fell in love and formed relationships after their “affair.”
Several women specifically urged me to investigate how “women seeking women” were handled in the database and code. Many had met other women for threesomes with men, or just for a lesbian romp outside their heterosexual marriages. I decided to take their advice, because now it was clear that a lot more women were active in the membership than I initially believed.
What I found was that there are over 770,000 women seeking women in the database, out of 5.5 million women overall, and none of them are hosts. That’s 14 per cent, much higher than the estimated 1.5 per cent of lesbians (and .9 per cent of bisexuals) in the U.S. population. These may not be active accounts, but they don’t appear to be Ashley Madison engagers either. If there are real women behind these accounts, we know they aren’t getting bombarded with bot messages. Bots avoid women. And comments in the code reveal that “woman seeking woman” profiles aren’t shown to straight men. It would seem that the only members of Ashley Madison who aren’t inundated by spam and randos are women who seek trysts with other women or couples.
There are also about 345,000 men seeking men in the database, and we know from the patch I mentioned earlier that developers were working hard to prevent the engagers from harassing these guys too. It’s possible, as one person put it to me in email, that Ashley Madison was actually a pretty decent hookup site for gay people — but that was mostly because the system was designed to ignore them.
In fact, there are only 5 possible categories of desire allowed in the Ashley Madison code. Here they are, from a comment:
1: Attached Female Seeking Males
2: Attached Male Seeking Females
3: Single Male Seeking Attached Females
4: Single Female Seeking Attached Males
5: Attached Male Seeking Males
6: Attached Female Seeking Females
Note that you can’t be a single woman seeking attached women, nor a single man seeking attached men. Nobody building this source code thought very hard about options for gay people.
Nobody thought much about women either. Now that we know how rarely women were contacted by bots, it seems certain that any human woman on the site would have been able to meet human men with little difficulty or interference. There is a certain freedom in being the group that is ignored the most. Hiding in a haze of spam bots, women were connecting with each other and with men. We don’t know how many, nor how often, but we know they were doing it.
That said, a huge portion of Ashley Madison’s software development efforts are aimed at refining their fembot army, to make it seem that women are active on the site. Either they did this because the number of real women was vanishingly small, or because they didn’t want men to hook up with real women and stop buying credits from the company. Whatever the reason, it appears that the Ashley Madison money-making scheme was bots all the way down.
Art and data tables by Tara Jacoby
