Active on Google Play Store as recently as last Friday, a mobile banking Trojan infected thousands of users who thought they downloading games or innocent-looking apps, according to research published by a trio of cybersecurity firms.
Photo: Getty
The malware, known as BankBot, was concealed inside various torch and Solitaire apps, and was first detected by researchers on October 13. After downloading an infected app, the Trojan would activate and wait for users to log in to pre-selected banking apps, including those of Wells Fargo, Chase, CitiBank and DiBa (ING). In some cases, bank transaction authentication numbers (TANs) – a form of multi-factor authentication employed by some banks – were intercepted in text messages.
Research into BankBot’s latest capabilities was conducted by employees at Czech cybersecurity firms Avast and ESET, and the Amsterdam-based SfyLabs, which focuses on Android-specific threats.
Although Play Protect scans the apps uploaded to Google’s app store against known malicious software, BankBot circumvented this defence by hosting its payload on a command and control server. After users downloaded one of the infected apps, such as “Tornado Flashlight”, the malware waited for two hours before downloading the payload. Phones that were not set to automatically accept files from unknown sources were prompted to accept the installation, Avast said.
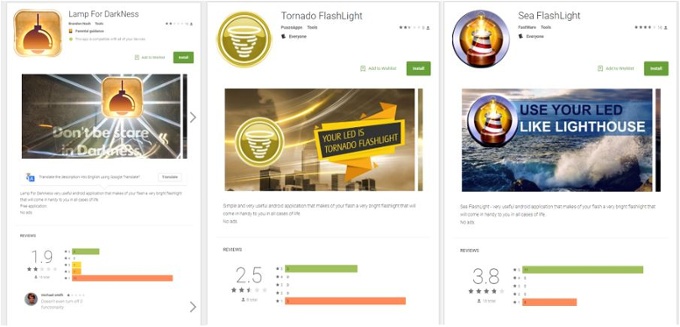
A few of the flashlight apps hosting BankBot (Avast)
The Android apps containing the malware were disguised to mislead users into believing it was a Google Play or system update requesting administrative privileges.
From there, BankBot quietly waited for users to log in to one of the aforementioned banking apps. Once the banking credentials were entered, they were immediately shared with the criminals who launched the malware campaign.
Certain banking apps send users security codes via text messages, which they have to enter into the app before accessing their accounts; however, this BankBot variant included a function that allowed it to intercept the texts and forward the codes to the attackers as well.
According to Avast, in addition to Australia, BankBot struck users in the US, Germany, the Netherlands, France, Poland, Spain, Portugal, Turkey, Greece, Russia, the Dominican Republic, Singapore and the Philippines.
“The malware is not active in the Ukraine, Belarus and Russia,” Avast’s researchers wrote. “This is most likely to protect the cyber criminals from receiving unwanted attention from law enforcement authorities in these countries.”
There are several steps users can take in the future to avoid having their bank accounts emptied, chiefly among them: Make sure your phone only allows downloads from trusted sources. At least then you can vet untrusted apps on a case-by-case basis. (Check under “security” in your phone’s settings.)
I can’t recommend enough just not downloading torch apps. They have a terrible reputation for hosting malware and it doesn’t seem like that’s changing any time soon. Just buy a torch.
[Avast]
