We’ve seen a lot of data breaches this year: some big, some small, some that are dangerous, and some that are just embarrassing. But if we were to name one as the creepiest data breach of 2017, this leak of logins for car tracking devices might take the cake.
Photo: Getty
The Kromtech Security Center recently found over half a million records belonging to SVR Tracking, a company that specialises in “vehicle recovery,” publicly accessible online. SVR provides its customers with around-the-clock surveillance of cars and trucks, just in case those vehicles are towed or stolen. To achieve “continuous” and “live” updates of a vehicle’s location, a tracking device is attached in a discreet location, somewhere an unauthorised driver isn’t likely to notice it.
According to SVR’s website, the tracking unit provides “continuous vehicle tracking, every two minutes when moving” and a “four hour heartbeat when stopped.” Basically, everywhere the car has been in the past 120 days should be accessible, so long as you have the right login credentials for SVR’s app, which is downloadable for desktops, laptops, and almost any mobile device.
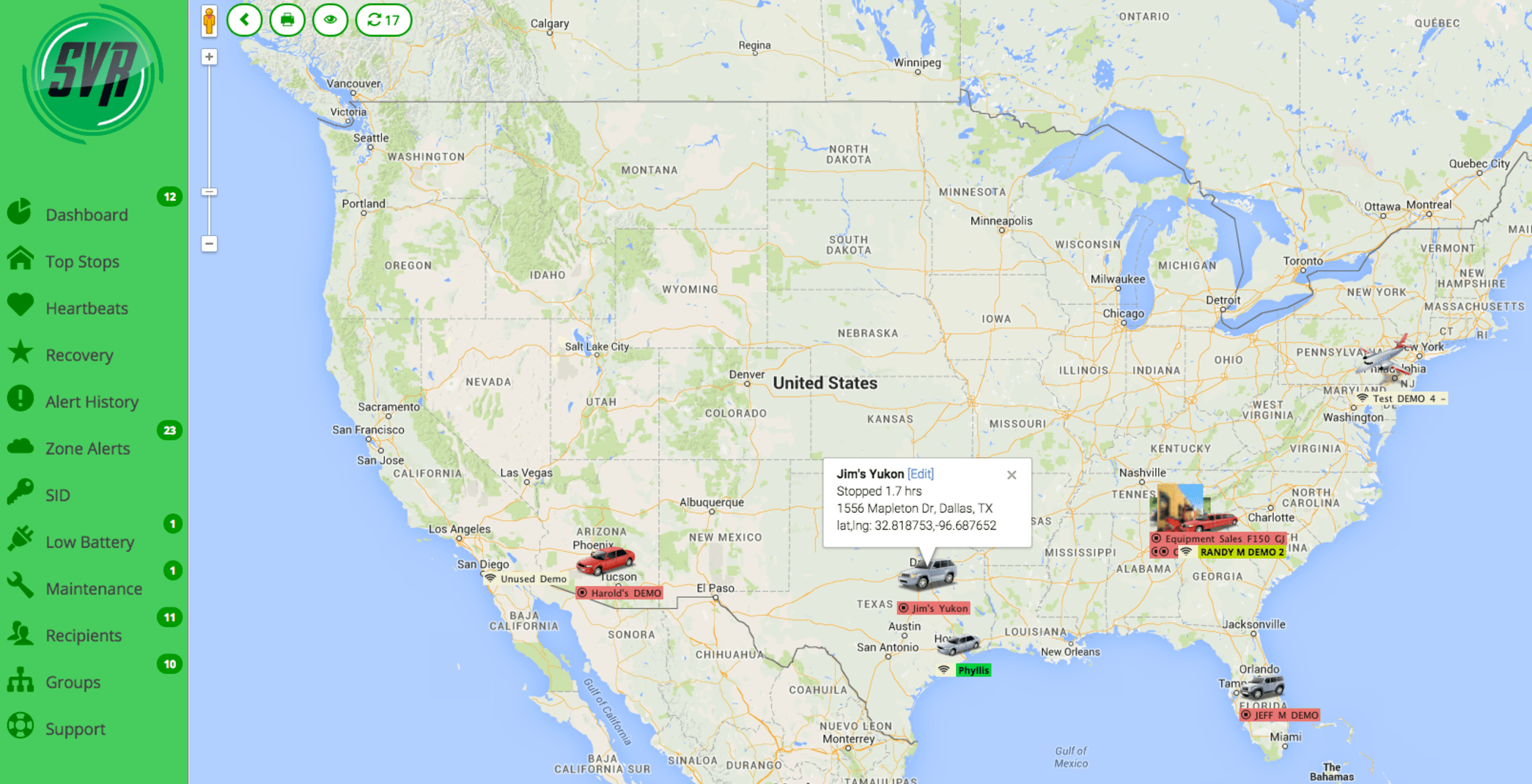
SVR app screenshot (svrtracking.com)
Kromtech discovered SVR’s data in a publicly accessible Amazon S3 bucket. It contained information on roughly 540,000 SVR accounts, including email addresses and passwords, as well as some licence plates and vehicle identification numbers (VIN). There were half a million records overall, Kromtech said, “but in some cases credentials were given for a record with several vehicles associated with it.”
The SVR passwords were hashed — or scrambled with other random data — but only using the weakest protection level (SHA-1), meaning it wouldn’t take a proper hacker much time to crack them. As with most data breaches, it’s difficult to say for how long the data was actually exposed.
“The overall number of devices could be much larger given the fact that many of the resellers or clients had large numbers of devices for tracking,” said Kromtech’s Bob Diachenko. “In the age where crime and technology go hand in hand, imagine the potential danger if cyber criminals could find out where a car is by logging in with the credentials that were publicly available online and steal that car?”
The leak further exposed 339 logs containing a wide range of vehicle records, including images and maintenance records, as well as documents detailing contracts with more than 400 car dealerships that use SVR’s services.
Kromtech said it first spotted the data online on September 18th. It took roughly a day for the researchers to determine to whom it belonged. SVR was then notified on September 20th and within a few hours the server was locked down. The company did not actually respond to Kromtech, however, nor did it respond this morning when Gizmodo asked for a comment. We’ll update if it does.
Earlier this month, Kromtech discovered about four million records containing personally identifiable information of Time Warner Cable customers. That leak was also traced back to an unsecured Amazon S3 bucket. In another breach, unrelated to Amazon, Kromtech discovered more than 88,600 credit cards, passport photos, and other forms of ID exposed online. In May, the company announced the discovery of a massive trove of more than 560 million login credentials thanks to one misconfigured database.
[Kromtech]
