Photo: Getty
Ripping the faces off ATMs and injecting them with malware is great fun, sure, but not so much when you get caught by a security guard and tossed in jail. For these reasons and more, many cyber criminals are turning to a less than hands-on approach and attacking ATMs remotely instead.
In its latest cyber threat report, Trend Micro’s researchers highlight the growing number of network-based attacks targeting ATMs; what the multinational security software company dubs a “shift in the malware landscape.” These attacks, which can cause ATMs to spit out tens of thousands of dollars, differ from skimmers, fake keypads, and malware injected on site, in the way that they require no physical interaction with the machine.
Criminals further benefit from remote attacks because virtually any ATM is a target, whereas physical tampering typically requires privacy — accessing the machine at night, in a dark alley or corner, somewhere concealed from potential onlookers and cops. A remote attack doesn’t need to carried out in the dark of night; a cash mule can approach any ATM and, without close inspection, appear to be engaged in legitimate ATM activity.
In evaluating how ATM malware has evolved, giving criminals today the ability to essentially produce cash whenever and wherever they want, Trend Micro partnered with Europol’s European Cybercrime Center (EC3) to pick apart some of these newer, stealthier techniques. As a prominent example, the researchers pointed to the Ripper malware attacks of yesteryear, in which 12.29 million baht (about $346,000 USD ($440,487)) was stolen from 21 ATMs in Thailand. Ultimately, around 10,000 ATMs were ultimately found vulnerable to the Ripper virus.
Trend Micro, Europol
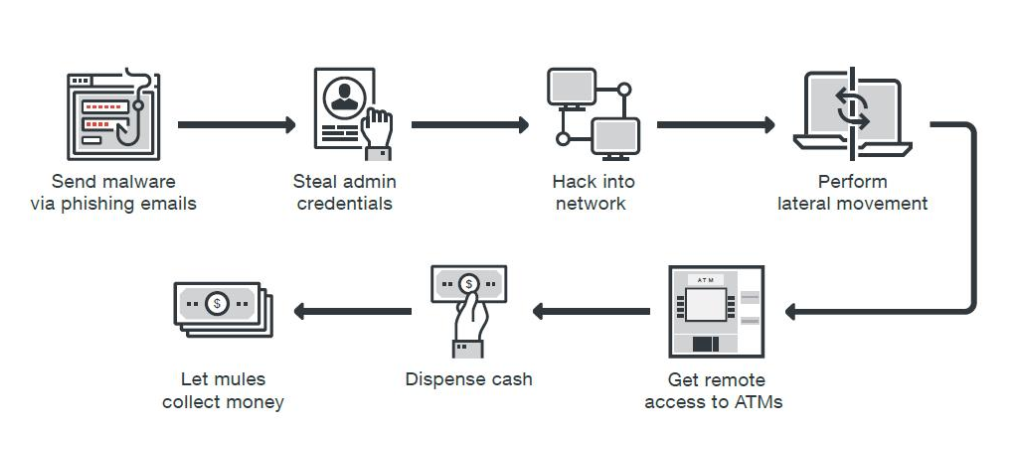
As Trend Micro notes, network-based attacks aren’t as easy to pull off and, of course, hacking remotely carries inherent risks; obfuscating one’s identity online may not be as simple as, say, slipping on a pair of gloves and a mask. The process of invading a bank, too, is itself fairly complex. Employees are a common vector; human beings being notably unreliable, the weakest link typically in any company’s security.
Phishing emails containing malicious executables are the preferred method for capturing a bank employee’s credentials. Once the hackers gain access, they can move laterally through the bank’s network to gain control over the ATMs. “Some malware families even have self-deleting capabilities, effectively dissolving most traces of the criminal activity,” Trend Micro notes.
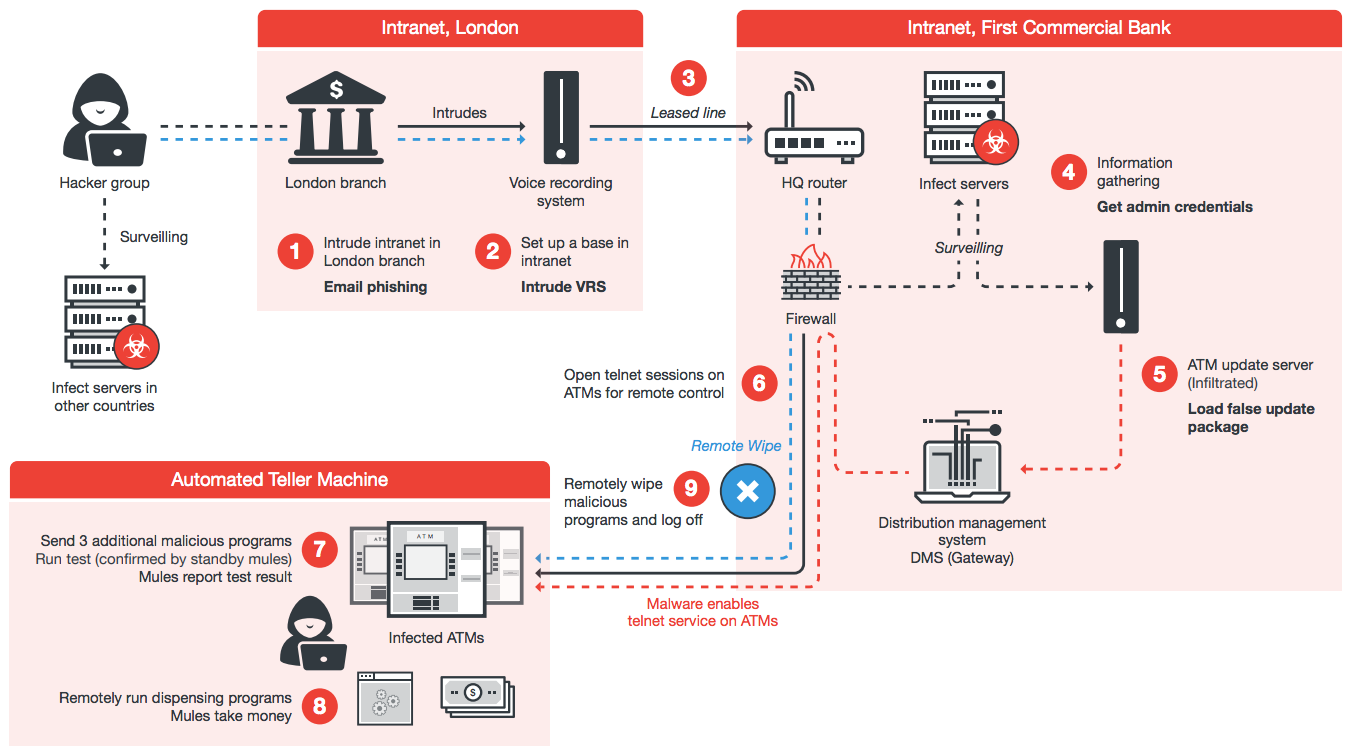
Another prominent example is the July 2016 attack on First Commerce Bank. Roughly the equivalent of $US2.4 ($3) million USD was stolen from 22 branches in Taiwan. The hackers never touched the machines.
The attack was incredibly sophisticated: It began at the bank’s London branch. The hackers used the bank’s voice recording system to steal the domain administrator’s credentials; used those credentials to hack the company’s VPN, bypassing firewall ports to gain access to the Taiwan branch’s network; and once inside, they located the system for updating ATM software. Using a fake update package, the hackers then enabled telnet service on the machines, which allowed them to uploaded various programs for testing the ATMs and eventually force an unauthorised withdrawal.
Meanwhile, cash mules stood by, communicating with the hackers over an encrypted chat and reporting the results of the tests. Once the machines spit out the cash, the mules gathered it up and moved on to the next machine. “In the meantime, the remote hackers wiped the malicious programs off the victimized ATM and logged off,” the researchers said.
Trend Micro, Europol
“It could be that these are regular criminal groups that already had access to the bank’s network and eventually realised that they could hop onto the ATM network,” the report states. “In Ripper’s case, though, it shows that some of these criminals are specifically looking for the ATM network as a target and not stumbling upon it by mere chance. These gangs have both the inclination and the technical knowledge to target these machines over any other resources of the targeted bank.”
“While network attacks have not been reported in bigger regions such as the United States and Canada,” the researchers add, “we believe this to be a new tendency that is probably going to consolidate in 2017 and beyond.”
