Image: Денис Евстратов/Unsplash
As if there aren’t enough tech security threats to worry about, you also need to be on your guard against so-called ‘stalkerware’ — those invasive types of programs installed by suspicious spouses, jealous exes or controlling parents without your knowledge. Here are the warning signs (on your computer) to look out for, and what you can do about them.
Stalkerware explained
Stalkerware as a term only recently gained traction thanks to a powerful series of posts on Motherboard, though the practice of installing software to spy on family and friends has been around for much longer than that. Now these tools are more readily available and more sophisticated than ever before. Which means it isn’t just hackers who can use them to chronicle your online life.
The rise of the smartphone has played a part in these kinds of DIY surveillance operations — get access to someone’s mobile, and you can spy on their lives in unprecedented detail, from the text messages they send to the photos they snap. Before you could snoop on someone’s email; now, you can know where they are at all times.
Motherboard looked at a piece of software called FlexiSpy, which can run in the background on computers and phones, collecting a dossier of data for a third party, whether a jealous lover or protective parent — and there are plenty of others like it.
If you suspect that FlexiSpy or similar stalkerware has been installed on one of your devices, the effects can be emotionally and psychologically crippling. Don’t be afraid of seeking support from friends, family, and resources like the National Domestic Violence Hotline if you feel like you need to (and as well as following the steps we’ve laid out here).
Stalkerware warning signs
The slightly reassuring news is that it’s very difficult for someone to install stalkerware without having physical access to your phone or computer. It can’t be magically installed through the air or transported via a text message without you responding to it — modern-day OSes are too security-savvy to allow that to happen.
You might inadvertently install something you don’t want, whether stalkerware or a standard virus, by following a link in an email, so, as always, be very suspicious of links you get over email or social media. Avoid unknown senders and double-check files with known senders — particularly when sent unsolicited. Unfortunately, most stalkers out there probably won’t try this method for fear of giving the game away.
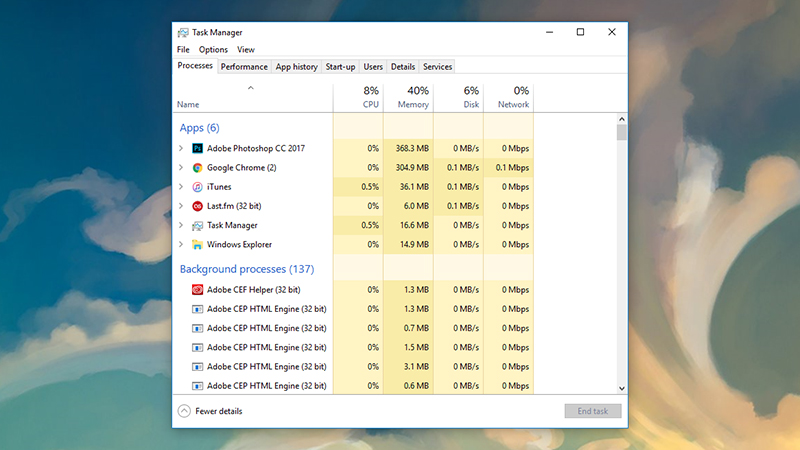
Image: Screenshot
The first warning sign to look out for is if your laptop or phone has been borrowed for an extended period of time by someone else — and perhaps come back with settings or apps or changes that you don’t recognise. On Windows, you can see apps running in the background by right-clicking on the taskbar and choosing Task Manager; on macOS, launch Activity Monitor from Spotlight.
A quick web search for any apps or processes you don’t recognise in Task Manager or Activity Monitor might flag up stalkerware — this is a good method for catching all kinds of security threats, but it’s by no means guaranteed to catch everything.
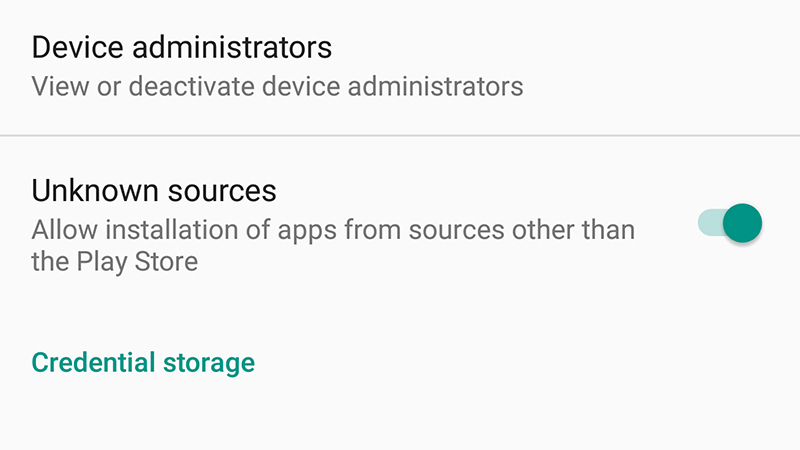
Image: Screenshot
In the case of phones, most deep-lying monitoring tools require a jailbreak (on iPhones) or for you to enable apps from unknown sources (on Android), because of the extra system access that grants — if you’re on an iPhone, the presence of the Cydia app or an old iOS version that can’t be updated are signs that this is what’s gone on with your handset. On Android, head to Security in Settings and see if the Unknown devices toggle is set to On.
Not all kinds of stalking require an app though. If someone close to you knows the kind of words you use for passwords and can have a pretty good stab at your security questions too, then they might be able to get at your email or social media accounts.
Which means you should probably check on what devices have logged into your accounts and when.
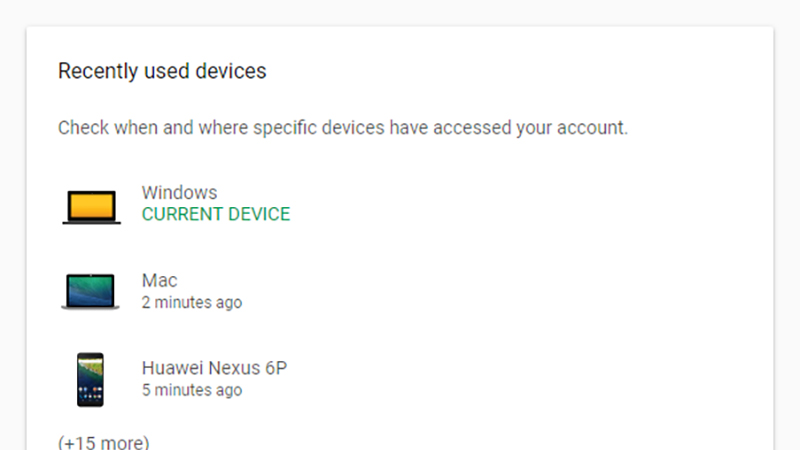
Image: Screenshot
If the services you use let you check up on active sessions, then do this: From your Google account page, for example, click Device activity & notifications to see computers and phones that have recently accessed your account. On Facebook, meanwhile, you can head to Security and login from the Settings page to see active sessions and log out from them.
In general, trust your instincts — it’s possible that whoever is doing the stalking will let something slip or drop a hint before you notice anything amiss in your email account or on your smartphone. Whether or not you can get hold of any proof to begin with, trying to remove the offending app or apps can confirm your suspicions either way.
Stalkerware removal
By design, stalkerware is very hard to spot and remove, but you do have a few options if you think someone is spying on you. If you suspect your email is being monitored, for example, then dive in and change your password to something new, and change your security reset questions too. Switching on two-factor authentication will help as well, as they will need physical access to your devices in order to alter passwords.
If you believe that you’ve been hit by the FlexiSpy stalkerware in particular, then the FlexiKiller tool developed by Claudio Guarnieri at activist group Security Without Borders, should be able to remove it from your Windows or Mac computer. It’s not the most user-friendly of applications, but follow the supplied instructions carefully, and you should be fine.
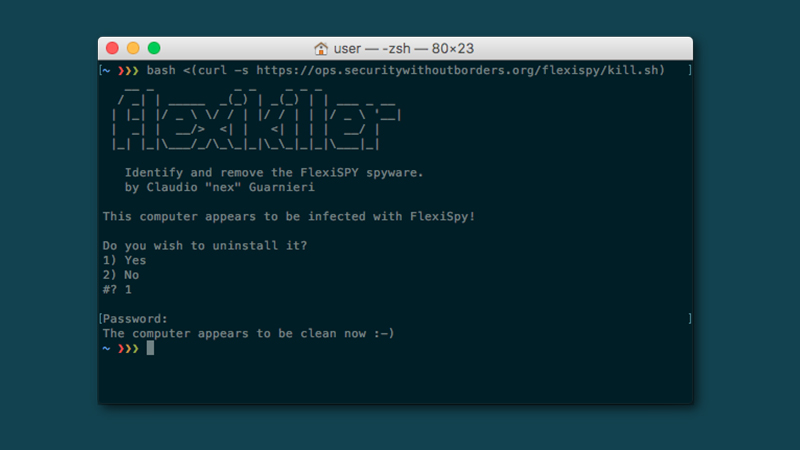
Image: Screenshot
More generally for computers, the advice is the same as it is for fighting any kind of virus or malware threat: A keylogger installed by a hacker works the same as a keylogger installed by a stalker. Keep a competent security tool installed, update it regularly, and scan often. If you think your current software is missing something, on-demand scanners like Microsoft Safety Scanner or Kaspersky Virus Scanner can help.
If you suspect your webcam is being activated without your knowledge, programs such as OverSight for the Mac are worth installing. We haven’t found a comparable tool for Windows recently, but if you open up Settings in Windows 10 then click Privacy and Camera, you can see which apps can use your webcam. It’s possible you can catch some sign of the stalkerware without actually revealing the whole program.
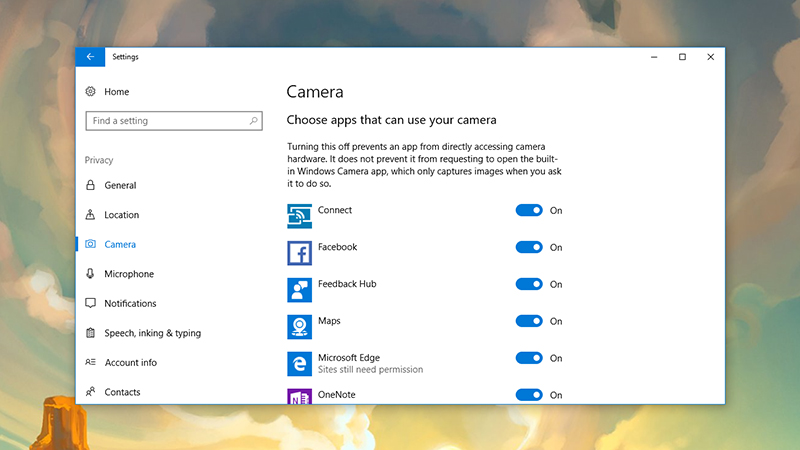
Image: Screenshot
When it comes to phones, a complete factory reset should be enough to clear out most monitoring software, though it’s hard to say for certain as we’re not privy to all of the surreptitious tools that are out there. As far as jailbroken iPhones go, resetting them back to their factory condition will remove the jailbreak along with all of your apps, wanted or unwanted, and all your files.
On the latest version of (stock) Android, open Settings and go to Backup & reset then tap Factory data reset. On iOS, you need to plug your phone into a computer running iTunes and then reset it from there, using the Restore iPhone option. In both cases remember to backup all of your important files and photos somewhere else first, and unregister your phone from services like iMessage and Find my iPhone if you need to.
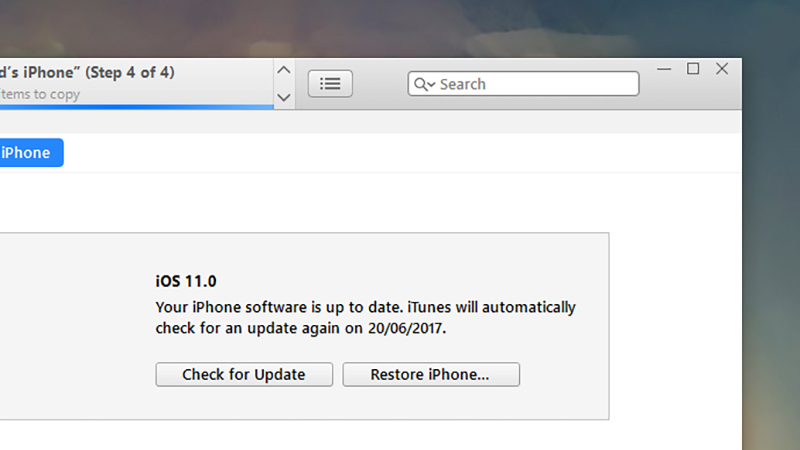
Image: Screenshot
Keeping an eye on the apps installed on your phone is a good idea too. On Android, it’s the Apps menu in Settings; on iOS, you can go to General then Apps to see what’s installed. Again, use a quick web search to look up anything you don’t recognise or remember installing to see if it’s anything you need to worry about.
By its very nature, stalkerware is designed to be well-hidden and hard to detect, but it’s difficult for something to stay on your laptop or smartphone for long if you’re specifically looking for it. Getting rid of whatever’s been installed on your device is only part of the process of dealing with being spied on, but you can at least make sure the stalkerware itself is taken out.
