I like a good strong password just as much as anyone else. But CNBC’s stunty idea for a tool that tested the strength of people’s passwords is one of the stupidest things I’ve seen in days — possibly weeks!
A columnist for CNBC’s The Big Crunch tried to make a misguided point about the FBI’s iPhone situation with an interactive tool that asked readers to input their password to see how secure they were. The post is now down, but if you did comply with the CNBC request, it might be a good idea to change your password. You should do this from time to time anyway.
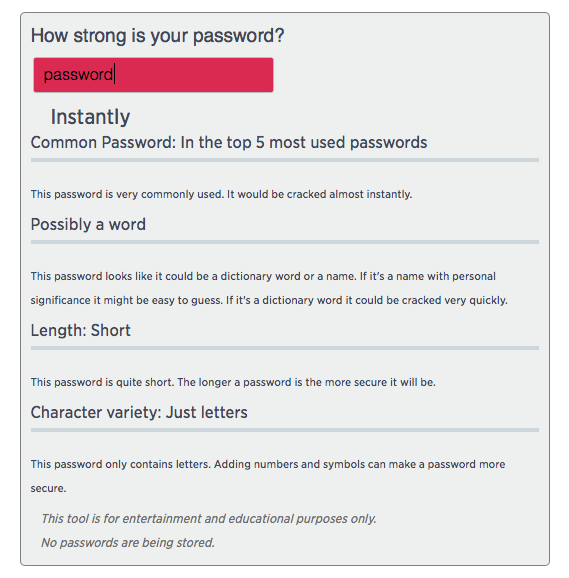
The post asked you to type your password into a field, hit enter and voila! CNBC’s expertly coded widget provided detailed analysis of that password, telling you whether it was strong, and if not, what was wrong with it.
I know what you’re thinking: Come on, this was only for “entertainment and educational purposes”, as the widget clearly stated in official-looking italic text. What could go wrong? Well…
Holy crap: @cnbc now sends your test passwd to all 3rd parties when you hit enter @__apf__https://t.co/rOQuvJ4KE2 pic.twitter.com/diRjcvJ919
— ashkan soltani (@ashk4n) March 29, 2016
A few people on Twitter claimed the widget is an insecure form that actually submits the characters you enter into the text field to third parties. Whether they’re right or not, you should never enter your password into some random internet form.
But is CNBC actually putting people at risk? I asked our in-house expert Adam Pash, the developer who runs Gawker Media’s Editorial Labs, for his take. He said although it’s unlikely, yes, someone could use this tool to get your password.
Since it’s a form field, it reloads the page when you hit “enter”, changing the url and, in effect, saving the password you just typed in.
So for example the original URL is:
http://www.cnbc.com/2016/03/29/apple-and-the-construction-of-secure-passwords.html
After you enter asdfasdf, the page refreshes and the url is:
http://www.cnbc.com/2016/03/29/apple-and-the-construction-of-secure-passwords.html?name=asdfasdf
“In theory, if there’s someone sniffing traffic on your network, they could see these urls being requested in plain text, and then try sniffing on other traffic coming from you that might indicate some account information,” Pash told me. This could be as easy as finding out your email address. And it wouldn’t be hard for these ad trackers to collect a bunch of people’s passwords in their logs.
So while CNBC’s cool tool is not necessarily malicious, it’s more just sloppy. “I’m not sure it’s a serious threat,” says Pash. “But it’s definitely dumb.”
It appears CNBC has realised it’s dumb too, because this is what you get when you try to find the story now:

We’ve reached out to CNBC for comment but had not heard back at time of writing.
Meanwhile, this tool seems totally legit.
Just working on my new news app. pic.twitter.com/60Z3grWtB7
— Jeremy Bowers (@jeremybowers) March 29, 2016
[CNBC]