On Wednesday evening, the news began to break on Twitter. Computer security analysts had discovered something nefarious about a piece of advertising software called Superfish, which comes pre-installed on cheap Lenovo laptops like the Yoga 2. Superfish was leaving the laptops wide open to takeover by malicious adversaries. And it was all being done to deliver internet ads.
Lenovo, trusted manufacturer of low-cost, popular laptops like the Yoga series, quickly found itself embroiled in a scandal. The company had done a deal with adware maker Superfish to install its software on its machines for a period of months. Lenovo would get money from Superfish by allowing it to feed ads from its partners onto the web pages that consumers visited. The problem? Superfish’s product was turning Lenovo laptops into soft targets for criminals.
Discovering Superfish
The trouble started when Facebook engineering director Mike Shaver commented on Twitter:
Lenovo installs a MITM cert and proxy called Superfish, on new laptops, so it can inject ads? Someone tell me that’s not the world I’m in.
— Mike Shaver (@shaver) February 19, 2015
He was referring to a man-in-the-middle attack (MITM), a common form of malicious hack, which allows your adversary to jump right into the middle of your network communications. A typical MITM attack, for example, will monitor your traffic until you, say, query a bank website. Then it injects new data, redirecting you to a fake bank site where you type in your password — and you can guess what happens next. The idea that trusted computer maker Lenovo might be enabling a MITM attack to stick advertising into people’s traffic stream was pretty shocking.
Almost immediately, Google Chrome security researcher Adrienne Porter Felt began digging in the Lenovo help forums, trying to figure out what was going on with this Superfish thing. She works on the exact kind of issue Shaver had described, involving an attack where the bad guys put a fake “cert,” in this case a self-signed root certificate, into your browser. That fake cert tells your browser to trust a whole bunch of extra sites that Chrome, IE and Firefox would normally warn you to avoid. Basically, this fake cert means that browsers on Lenovo laptops trust any site that Superfish tells them to — including fake banks, fake insurance companies, fake Facebook, whatever.
What Felt discovered was that Superfish had been a topic of controversy for months in the Lenovo forums, causing users no end of headaches. After months of complaints, an official Lenovo spokesperson responded in late January, confirming that Superfish did indeed inject ads into your traffic. The rep called it the “Superfish Visual Discovery Engine,” and what it was doing was watching everyone’s network traffic, and adding advertising to search results when it figured out that they were shopping.
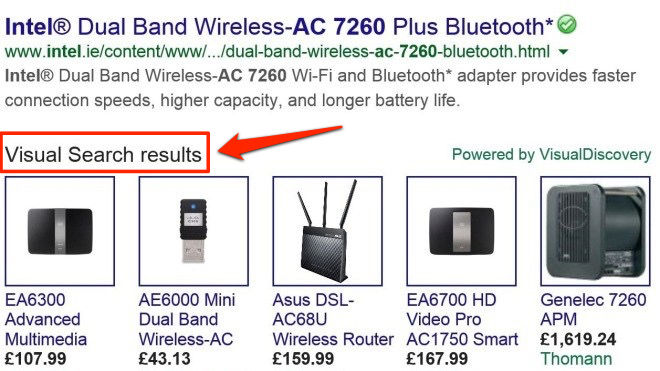
Above, you can see what your search results would look like with Superfish installed. Those “visual” ads were all injected into this user’s traffic in midstream. It’s the very definition of a man-in-the-middle attack, where an attacker injects new information into your traffic without you knowing about it. In this case, the new information was ads — but it could have been an entirely fake website.
Felt was appalled, and posted on Twitter:
Lenovo confirms they ship preinstalled software that injects ads into sites including google https://t.co/DIDMrgw62z via @shaver
— Adrienne Porter Felt (@__apf__) February 19, 2015
This set off a night of hacking among Felt’s colleagues and other infosec experts, to figure out what the hell this Superfish software was doing — and how bad the MITM attack really was.
It was bad.
By yesterday morning, the news had broken all across the internet: By pre-installing Superfish, Lenovo had left hundreds of thousands of customers vulnerable to MITM attacks that could leave their passwords and personal data in the hands of criminals. And that was on top of injecting annoying ads that often broke various other apps and led to those first customer complaints in the Lenovo forums last year.
But the worst was yet to come. An infosec researcher with Errata Security, Robert Graham, had spent his Wednesday night poring over the code that makes up Superfish, and discovered that the program wasn’t just malicious — it was also incompetent. There are a number of legitimate programs that do something like a MITM attack on your computer in order to look at your traffic as it’s moving between your computer and the internet. Anti-virus programs do this, for example, in order to detect certain kinds of malware.
Usually when an anti-virus program does a MITM with a fake cert, however, every installation of the anti-virus program generates a unique private key. Having a unique private key on your cert makes it a lot harder for bad guys to hijack your system. But Superfish? Its fake certs, on hundreds of thousands of computers, all shared the same private key. And Graham had found it, using a very quick, simple dictionary attack. Basically, he threw dictionary words at the program until one worked. The word that worked, by the way, was “komodia”, the name of the company whose MITM technique powered Superfish.
So let’s just step back and marvel at what this means for a minute. Essentially, anyone who has a Lenovo laptop with Superfish in it now has the keys to every other Lenovo laptop with Superfish. An adversary can drop $US600 on a computer, crack the password, and now she can do mass MITM attacks on every other Lenovo user. Felt’s colleague and fellow Google Chrome security researcher Chris Palmer explained on Twitter exactly what that would mean in a series of pictures.
#superfish pic.twitter.com/g6Q6MrRRpI
— Chris Palmer (@fugueish) February 19, 2015
Once you have the keys to the fake Superfish cert, you can use them to tell other computers that any site they visit is valid and trustworthy — because it has a Superfish cert, too! You know how when you go to a scammy site, Chrome, Firefox and IE will often send you a message that says the site is insecure or that its certificate is questionable? With the help of the Superfish MITM attack, you’ll never get those messages again — even when you are visiting a fake version of Bank of America, set up by bad guys to steal your login information.
Above, you can see a picture of a cert signed by Superfish for bankofamerica.com. Normal users would never see this screen, unless they dug down into their cert menus — which, let’s face, it none of us do for every single website we visit. But your Lenovo computer sees it, and trusts it, because of that fake root certificate. With Superfish, you have no guarantee that anything you see on the web is what it claims to be.
For their part, Lenovo has acknowledged that Superfish is a problem, and claims that they have stopped shipping it in newer computers. Still, several researchers were able to find Superfish two nights ago, in Lenovo laptops they had just bought.
It’s Official: Internet Advertising Is a Weapon
The question is, why would Lenovo do this? For money, of course. Superfish and other companies like it pay for the privilege of having their software pre-installed on your machines. Most of the apps you find pre-installed on your laptops, tablets and phones are from companies that paid to put it in front of your eyes, in the hope that you’d use their services or buy an upgrade. Normally this is an annoyance but not a security risk.
But with programs like Superfish, which affect other programs, users are harmed. You can un-install Superfish, but even when you do that, you don’t uninstall that fake cert that Superfish left behind in your browser. And that’s by design — Lenovo knew that would happen. But that’s also what makes their deal with Superfish so lucrative. Superfish knows it can keep serving ads for its partners for as long as most users have no idea what certs are, let alone that there can be a fake one that undermines their security.
To be fair, Lenovo is in a difficult position. In order to sell laptops in their Yoga line at such low prices, they pretty much have to make deals with companies like Superfish. That’s what subsidises the cost of making the laptop. You’ll notice that Superfish is not in any of Lenovo’s high-end lines like the ThinkPad. So not only are consumers getting screwed here, but it’s the consumers with the least amount of money to spend — students, retirees, and the working class. These are also people who are among the least likely to have the money or time to sue Lenovo for what the company has done to them.
The key takeaway here, though, is that the Superfish scandal is not an isolated incident — it’s just the one that has gotten the most attention in the media. Superfish and companies like it have been making malware like this for consumer electronics devices for years, leaving users vulnerable to attack. Over at Slate, software engineer David Auerbach points out that the last highly-public example of this kind of thing was when Sony put dangerous malware on its CDs to prevent unlawful copying.
In the case of Superfish, though, there are other dismaying elements to the story. Komodia founder Barak Weichselbaum, whose MITM technique is built into Superfish, is a former Israeli intelligence agent. Was Superfish also intended to aid intelligence agencies who wanted to spy on people’s internet traffic? Or was it merely based on techniques that Weichselbaum and his colleagues had learned while serving as intelligence agents?
Either way, Superfish suggests a disturbing connection between government surveillance and internet advertising. Even if Weichselbaum’s connection to Israeli intelligence is purely by chance, there is no denying that Superfish could have allowed the government to engage in MITM attacks — quietly snooping on all your internet traffic — just as easily as it could help criminals steal your passwords.
We’ve entered a strange time for the advertising industry in the high tech space. When hardware makers have to sell ad-supported devices like the Yoga, they open themselves up to shady deals that expose consumers to a lot of potential danger. We’re used to the idea that there are bad pieces of spyware and malware out there, buried inside internet ads — but now it could come pre-installed on the machines you thought you could trust.
If you are worried that Superfish is installed on your computer, you can learn more here about how to spot it and uninstall it.
