Fingerprints, blood spatter, muddy footprints, an errant hair. Every crime scene has its fair share of evidence. But not all of it is visible to the human eye, no matter how powerful the assisting microscope or black light. Some of the most damning evidence is mere bits and bytes.
Different kinds of investigations require different kinds of specialists, and data is no exception. Sure, any old flatfoot can turn on a working phone and cruise through some emails. But going any further than that quickly gets a lot more complicated. Sometimes the phone is locked. Or, better yet, maybe it’s utterly destroyed. That’s where the folks at Flashback Data come in.

One of the only data recovery and computer forensic firms in the country with the same kind of high-level accreditation as the FBI, Flashback Data is the last resort for problem phones that might be hiding secrets. Armed with an arsenal of specialised hardware and technicians who know their way around it, the firm rarely meets a phone whose guts it can’t spill.
We sat down with their team to learn a little bit about what happens when a phone shows up as evidence.

Your Lockscreen’s Not Worthy
Your little lockscreen pin might keep nosey friend/parents/siblings from perusing your secret stash of sexy/embarrassing/embarrassingly sexy photos, but for anyone who has a serious interest in getting into your phone, they offer precious little inconvenience and practically no real protection.
Sure, we’ve heard stories about the police being foiled by the old pattern-lock, but real professionals have bigger guns at their disposal. Getting inside isn’t just one trick, though; the magic bullet is a combination of couple different ingredients. First, the hardware.

These modest black boxes and their army of cables are the entry point into just about any secured phone. All you need to get started is a mastery of picking out the cable that fits into the port.
Using a combination of mostly secret, proprietary hardware tricks and probably a healthy dose of black magic, the gadgets get to work using the second piece of the puzzle: a special bootloader modified to rip through PINs and passwords like wet tissue paper.
When you power up your phone, the bootloader is the first thing that gets going. It verifies that everything else that comes on after (like your operating system) is secure and normal and on the up-and-up. Normally bootloaders come locked, so that you can’t load up deep, OS-level software the phone’s manufacturer isn’t cool with. You know, like software designed specifically to chew through security measures. Or custom ROMs.
That early entry is crucial. PINs, patterns, and even passwords are primarily designed to provide security against human beings; 10,000 codes (the total number of unique 4-digit PINs) is a formidable stack to work through when all you’ve got are two thumbs and a short attention span. But when you apply brute force — which is easy once you’ve got the right software on board — a 4-digit PIN barely registers as a nuisance; it only takes about 5 minutes to get past. Even relatively strong alphanumeric passwords won’t take longer than a few hours.
Fortunately, this kind of cracking hardware tends to be expensive and/or hard to come by, so it’s not a tool for commonplace thugs. Besides, commonplace thugs aren’t interested in you nearly as much as they are in selling your stolen phone. But when it comes to folks like Johnny Law, who are interested specifically in your data and are absolutely determined to get it, there’s not much your little passcodes can do to get in their way.
Raising the dead
It’s not always that easy; sometimes you need to get into a phone that’s bricked. Maybe a perp’s iPhone just happened to fall into a toilet, or his Droid “accidentally” got crushed by a hammer. That’ll make things a little more complicated, sure, but it’s far from game over. All you have to do is get the damn thing to turn back on somehow.
With the right amount of finesse, magnifying glasses, and soldering, most phones can be brought back from the brink. Then it’s back to the bootloader, and easy pickins. But sometimes that’s not even necessary. Do you use iCloud Backup? Sure, why wouldn’t you? That means there’s already an image of your phone out there, in a complete enough form that it’s plenty useful for forensics.
Should both of those methods fail, the phone is still in play; it’s just a little bit longer a haul. The first step of mining a phone that’s officially dead is to dig in and rip the data off its broken chip. Sometimes, this is as easy as slapping the chip into an adaptor and plugging it into a computer. Other times, it involves rigging up a whole jungle of wires to suck the data right out of the phone’s dead brain.
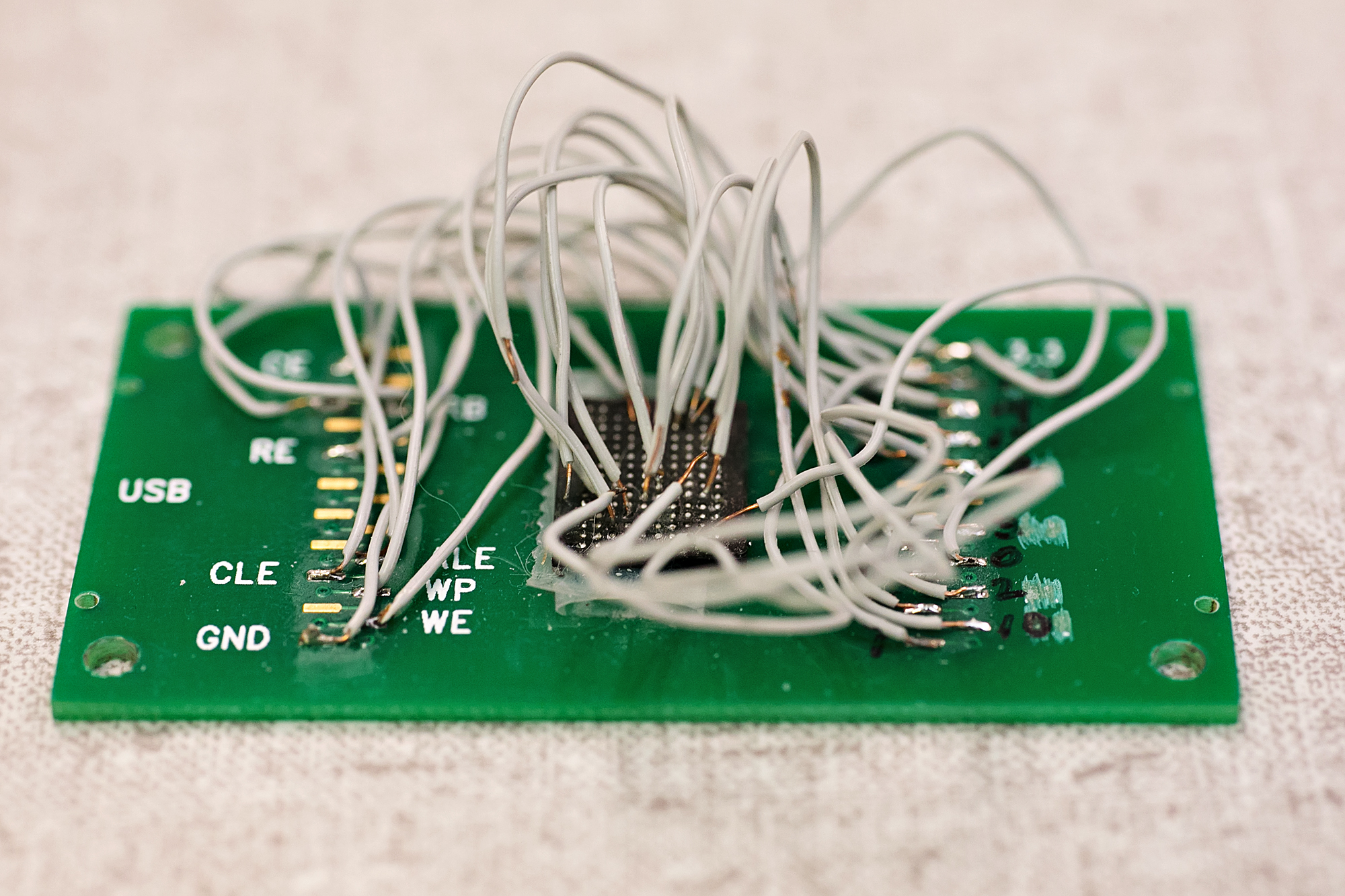
Reading Between the Lines
So you’ve gotten data off of a phone. Great! But not good enough. Understanding it is a whole other headache.
The memory on your phone is stored in a form that’s fit for machines, not humans, and the go-between is a small, integrated computer called the microcontroller. But with cases this dire, the phone’s microcontroller is generally dead as a doornail, so what you have after extraction is a whole mess of unreadable garbage data.
A good forensic tech might be able to spot bits and pieces of things here and there — like looking into the matrix through a screen full of code — but on the whole it’s still going to be unsable without some more massaging.
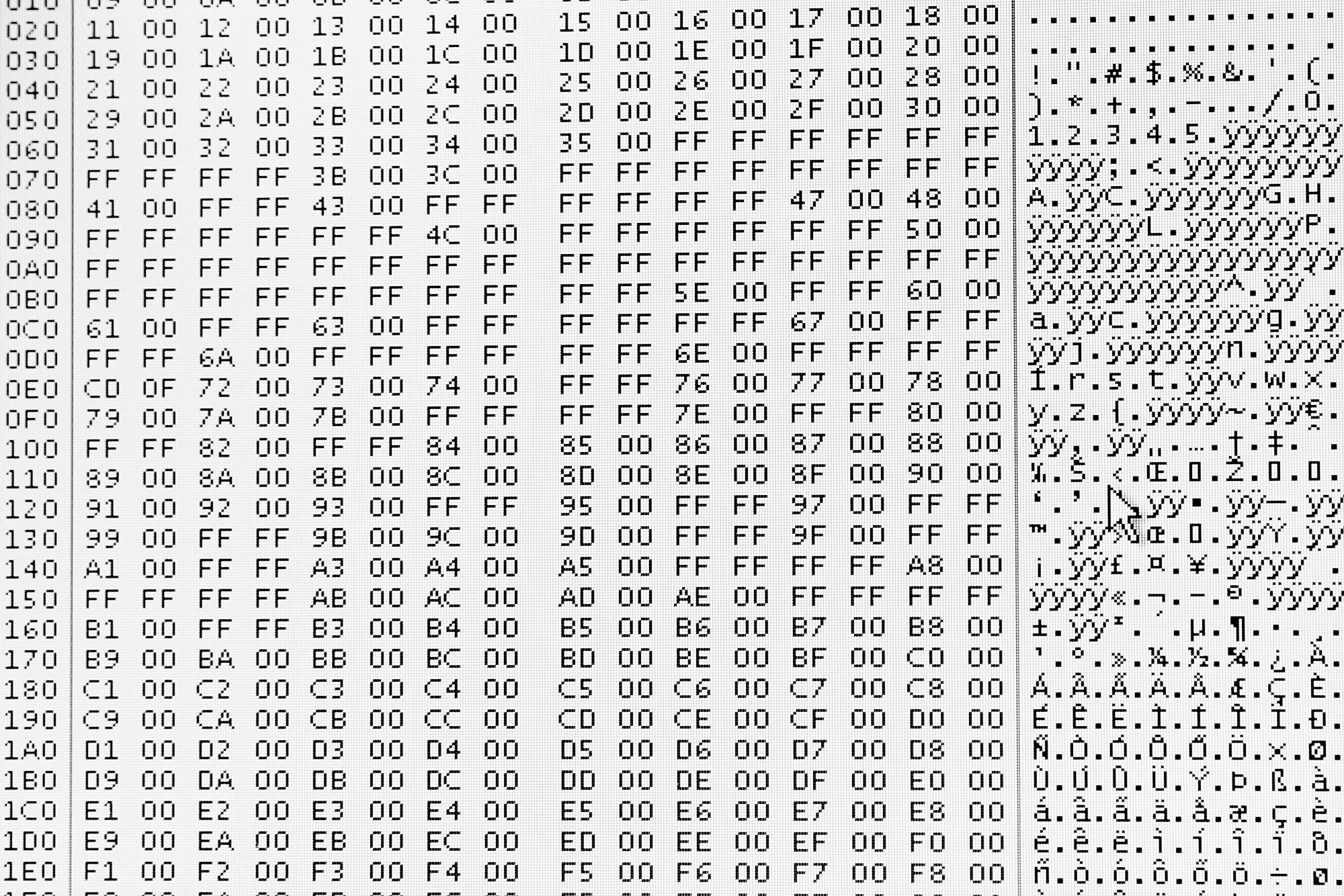
Where you can go from here largely depends on the phone. For most late-model iPhones, this is a dead end. From the 3GS on, iDevices sport default 256-bit AES encryption, stuff that’s (as far as we know) too tough for even the NSA to crack. Each handset’s unique key is burned right onto its silicon, so it’s not like it can get lost, but it means that the only way to get the data off the phone is to get the whole phone working again, microcontroller (and i’s device-specific unencryption abilities) and all. If the microcontroller is dead for good, there’s no hope for unencryption, and you’re stuck with this undecipherable chunk of encrypted digital slag. Criminals, take note!
If you’re working with an older iPhone, or an Android handset though, it’s possible to fake the microcontroller with special hardware, and translate from the chip’s machine language back into to something resembling human-readable data. Then, and only then, can the detective work really start.
Cybersleuthing
This part of the process is essentially the same kind of snooping you might do if a date left you alone with his or her phone, and if you are/were a creep. We’re talking the basics; reading through sent text messages and emails, looking at pictures and videos from the camera roll, digging through apps from private (or public) evidence of sketchiness.
By now, however, the physical phone has long since departed the scene. Instead, digital detectives are digging through clones of the each phone’s consciousness mirrored onto computers.
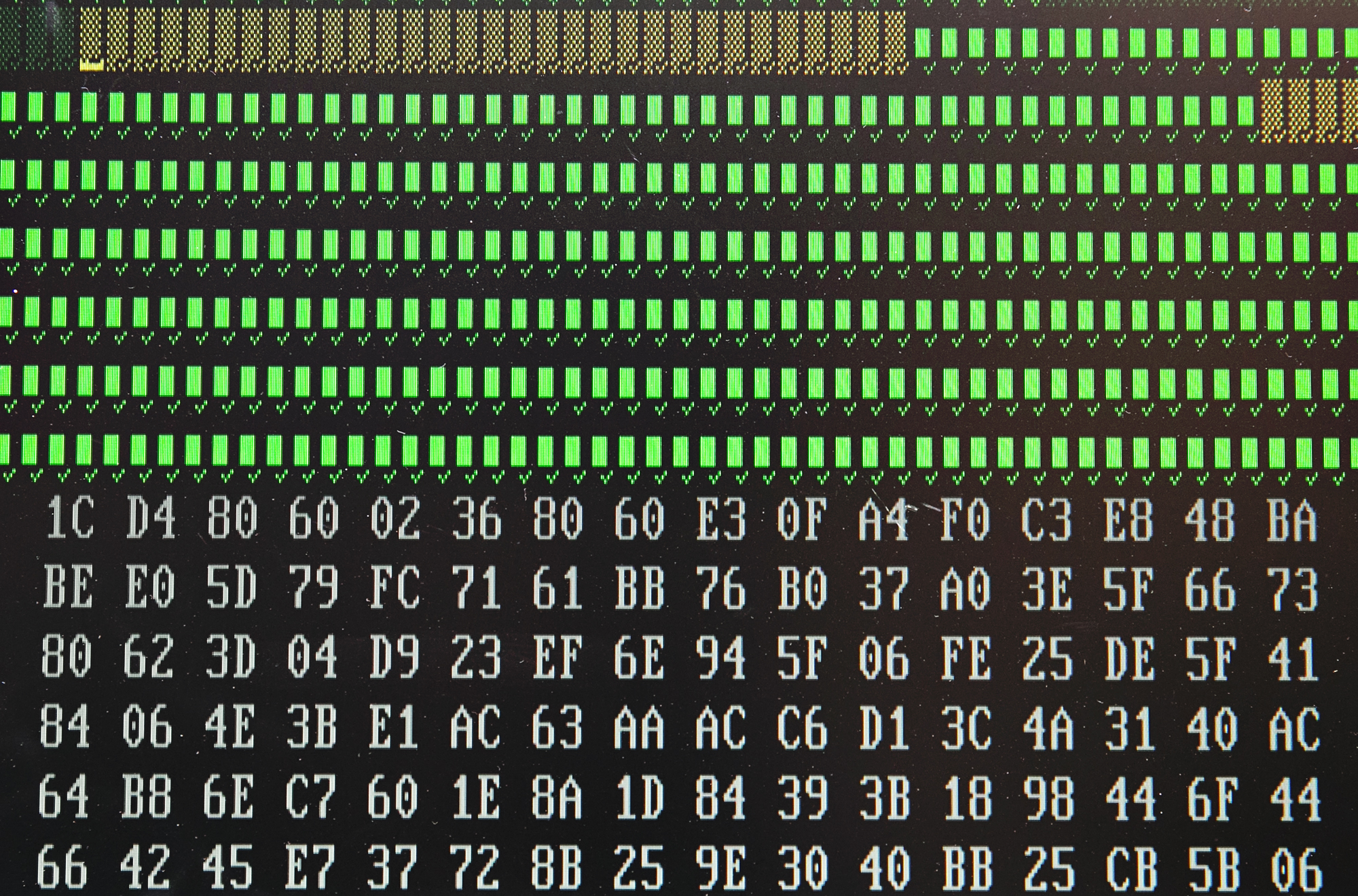
A consciousness being cloned
This serves a couple of purposes. For one, it means that the physical evidence that is the phone can stay locked away somewhere secure and free from tampering. It also means that there’s no risk of polluting the digital crime scene; if you’re cracking away at a copy of a copy, there’s no risk of accidentally treading through a puddle of digital blood. But most importantly, it lets you see deep into the phone’s very soul, beyond the thin veneer of unmodified call history and undeleted texts and photos.
It shouldn’t surprise you to learn that what you “delete” on your phone isn’t actually deleted; it’s brushed under the rug. When you pull up your messaging app or your phone’s gallery, you aren’t opening a closet door and looking inside. Instead, you’re looking at a list of what’s in that closet. Likewise, when you delete something, it’s not being taken out of the closet and destroyed; it’s just getting erased from the list. It’s still in there, packed away with digital mothballs.
Over time, that space in your phone’s memory gets reallocated. Bits that aren’t being used on the master list are taken, one by one, to make new pictures and new texts. But until duty calls, they just sit there with the old “deleted” data on them.
Finding those fragments and making them back into something halfway meaningful still takes a little work though. With special software that combs through code at the hex level, professionals can start to pick up on broken fragments of something that might be worth looking at, whether it’s half a .jpeg or a few choppy seconds of video. Eventually, you learn what to look for; Flashback Data even has its own hacked-together system specifically for decoding decaying emojis. One winky-face can speak volumes.
Paperwork IRL
Resurrecting gadgets from the dead and probing their every corners for hidden secrets is fun and all, but ultimately — like all good legal work — it boils down to paperwork. When it comes to computer forensics, the actual search and recovery is only building up to a final burst of thrilling documentation.
For private jobs — mostly hush hush corporate gigs — simply retrieving the lost data is enough. Criminal investigations, though, have a cascade of consequences. Phones that are evidence have to be very carefully controlled, their whereabouts recorded at every turn, movements from the closet to the workbench and back again noted, the processes behind digging up certain nuggets of data meticulously described so that they can be reproduced. It’s a painstaking mashup of legal and scientific documentation.
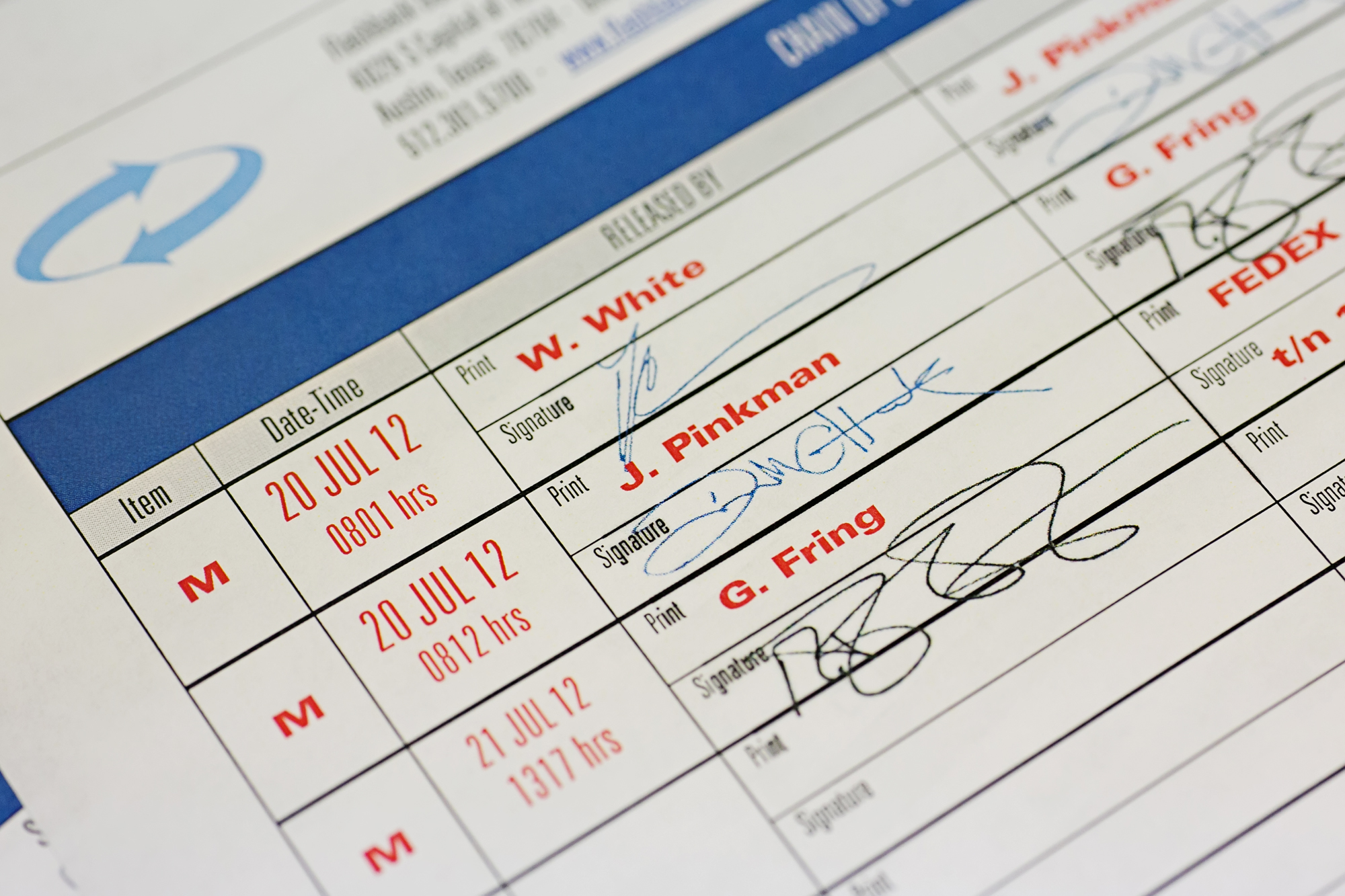
But in the end, that’s a minor if annoying layer on top of the technologically wizardry that’s at the heart of rescuing unique and irreplaceable data that can be the lynchpin in a mystery, offering first-hand info on whodunit, howtheydunit, and even whytheydunit. A phone can provide invaluable first-hand testimony against its owner, and that’s data worth digging for.
So next time you confide in your trusty pocket companion, remember: no matter how dead you think that phone may be, the ghost of its data can always come back to haunt you. And Flashback Data are just the techno-necromancers to do it.
Pictures: Flashback Data
